
> What is WEB-200??
WEB-200 is an Offensive Security course that teaches students how to discover and exploit common web vulnerabilities, and how to exfiltrate sensitive data from target web applications. Students will obtain a wide variety of skill sets and competencies for web app assessments.
Students who complete the course and pass the associated exam earn the Offensive Security Web Assessor (OSWA) certification, demonstrating their ability to leverage modern web exploitation techniques on modern applications. A certified OSWA candidate is prepared to take on the Advanced Web Attacks and Exploitation (WEB-300) course.
> Side Story:..
A lot of people think when you work at Offensive Security, you are given special privileges during an exam…🤣 let me share with you a secret. There Is No Special Treatment for Any OffSec Employee. You Have to Read The Course Module, Take On The Labs, Book An Exam Through The Portal & Also You Will Have To Go Through Proctoring Verification & Your Exam Will be Proctored Until The End. There are no special privileges offered to Any OffSec Employees During Exams we all go through the same procedure just like every other student.
> The Boring Story begins…..
On May 6th 2022, I was granted access to Offensive Security Learn Unlimited which I started with PEN-300 journey. Two months into studying PEN-300, I realized I was not prepared for that exam since some part of this course is heavily dependent on C# programming. I took a step back asked myself these questions:
- How good is your C# skill??
- Are your AD skills good??
- Are you mentally prepared for OSEP?
With these questions in mind, I decided it’s best to switch to a different a course while preparing myself for PEN-300. On August 12 2022, I started with WEB-200 course materials. As usual you know my style of doing things… I jumped straight into pwning the labs without reading course materials. This method works best for me… Why? Because from this, i will be able to test out what I know against what I am about to study. Few days into the lab, I got stuck on exploiting XSS vulnerability my first box. Oops thought I know it all got to jump back to the course material🤪.

> Fast Forward: Course Materials & Labs…..
In the course materials, after trying my hands on some of the XSS example labs, I figured a way to exploit the XSS vuln. AT this point I knew exactly what to do/ the path to take… This secret path is Try lab machine, get stuck then jump to course material and read on the related vulnerability. This continued for some time till I was able to fully compromise 3/5 lab machines. At this point, I stopped both reading the course materials and trying the lab machines. A friend advised the best way to see things clearer is to try looking at the problem from both sides. What this means is… “master the skill of identifying same vulnerabilities from different angles”. One of the best platforms to study web exploitations apart from the WEB-200materials is PortSwigger I quickly created an account, looked through the PortSwigger labs for topics that appear in the WEB-200 course material. I spent close to a 45 days on PortSwigger labs… took much time that I anticipated because I had to manage work and study time. After spending 45 days on PortSwigger, I made a big progress solving a total of 60 labs
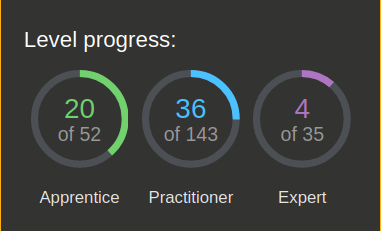
It’s time to test what I learnt from PortSwigger. Unfortunately, my focus was needed elsewhere (work😊)…. Early October, the work load reduced and it was time for another ride. Jumped back to the labs with the knowledge I acquired from PortSwigger. I made good progress on the labs but guess what, the WEB-200 course materials has a lot of goodies in it. I had to return to the course material to read more on vulnerability discovery and exploitation techniques. Armed with good information from both Web-200 course material and PortSwigger labs as well as the support from the OffSec Discord channel, I finally compromised the remaining labs. 5/5 OSWA Labs compromised while I’ve read through only 39.1% of the course materials.
> Discussion: Course Material vs PortSwigger Labs
Alright let me add my voice to this discussion…. I will start with PortSwigger labs, It is without any doubt that PortSwigger labs contain rich resources and it’s rated Number 1 on almost every blog that I have read but this doesn’t mean that you will do 100% fine without OffSec Lab Materials. In the Web-200 course content, I’ve learned a lot more than I could imagine about exploiting web application vunerabilities. In short, it was an eye opener.
OffSec did a great job in breaking down the explanations of all vulnerabilities and also provide exercise for all instances that’s mentioned in the course content. My best advice is: "These platforms offer an opportunity to learn. As far as you are learning something new and beneficial from these platforms/materials, I don’t think there is a need to argue/compare which one is the best/better" I have learnt a lot from these platforms and I will advise you to do same for your own good 🤗 Remember you are studying for yourself and not the community😜. Therefore, refrain from engaging in these poor arguments.
> Exam Preparations
> Note Taking and Site Bookmarking..
While studying on both PortSwigger and the OSWA course materials, I made sure I wrote down all payloads I used in both exercises and labs. Most times, I will include a small detail explaining why a payload will work or fail (I will talk about this later). Let’s take a look at a sample of my notes: 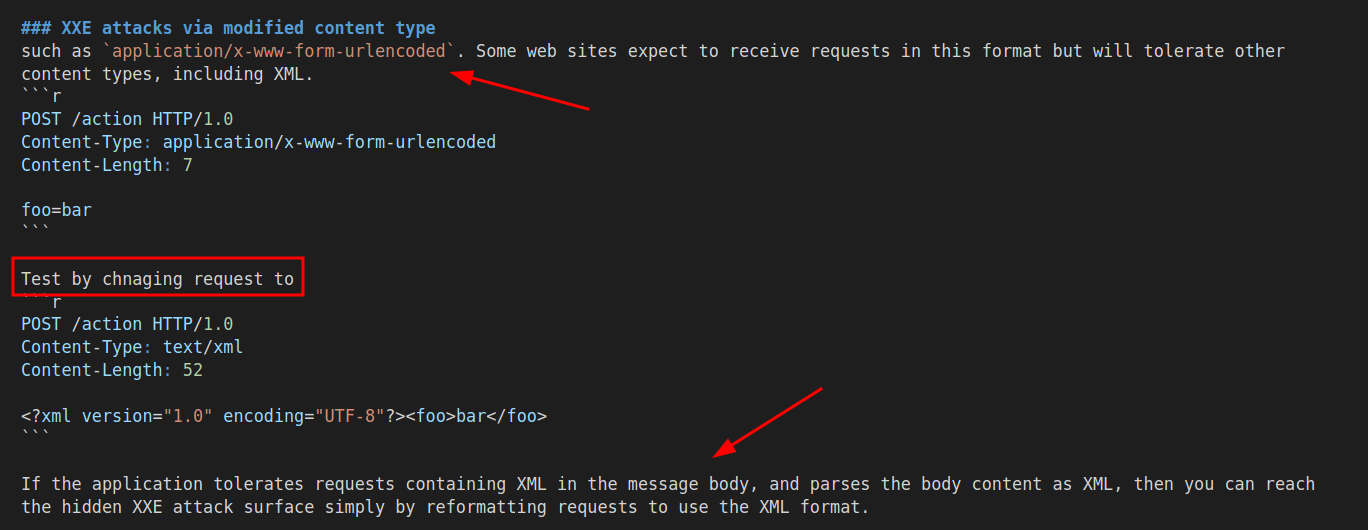
Using this method of note taking, I was able to accumulate a very big cheatsheet for web applications. Accurate note taking helped me a lot during my OSWA exam because there were instances where I will need to only copy and paste a payload with or without changing anything in the payload. This is a very important step and I will advise one shouldn’t rush to compromise/finish all the labs or exercises but rather taking your time to understand the vulnerability as well as discover multiple ways of exploiting that vulnerability.
Having this in mind, I made sure I went through all the course material not leaving any stone unturned. On November 28 2022, I completed almost all topics in OSWA Course material.
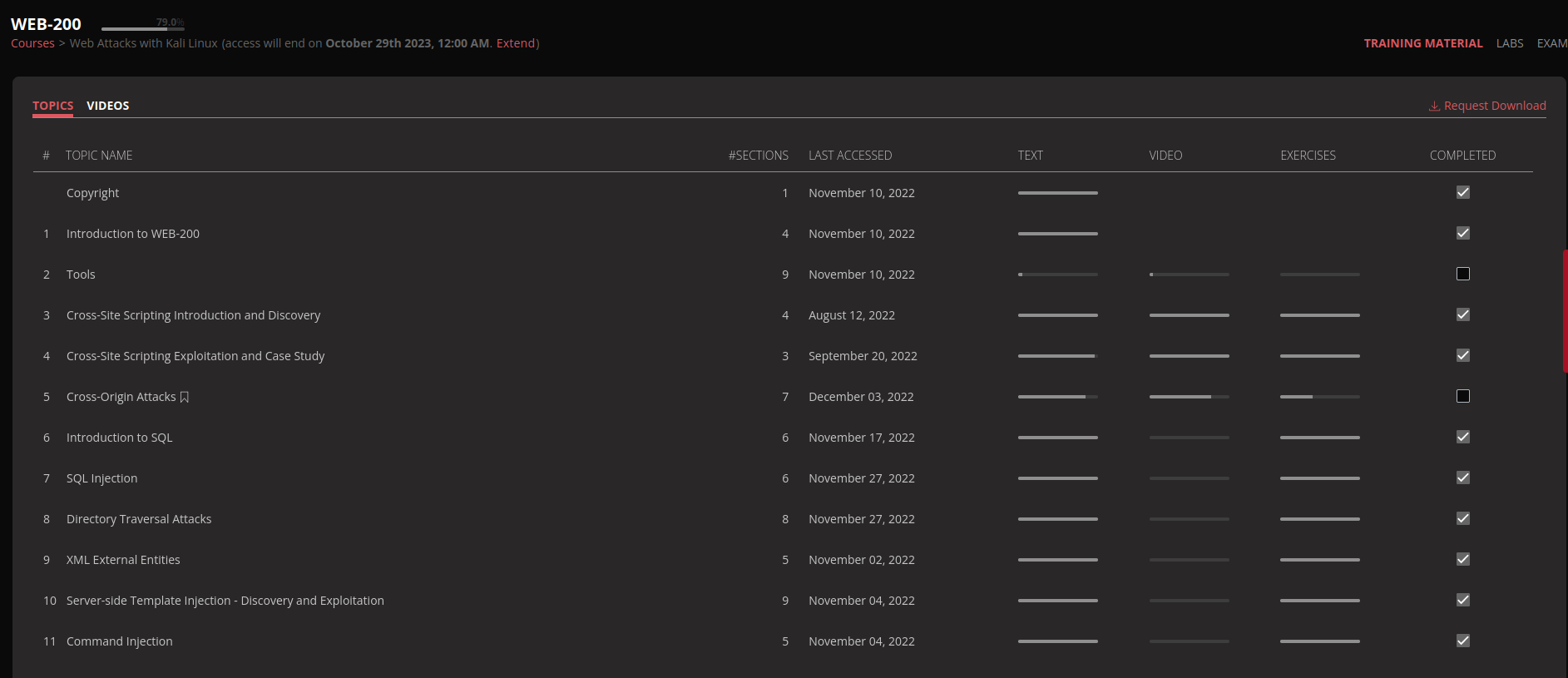
> Pre-Exam Tip..
Never assume that a vulnerability won’t be included to an exam lab. Otherwise, you risk ending up stranded like me in the exam. Because, the vulnerability i least expected to see turned out to be present on one of my exam machines. I nearly failed my exam because I was of the mindset that “There was no way it will show up.” Every vulnerability covered in the OSWA course is likely to be implemented on any exam machine… My advice is: “Stay concentrated, learn everything, understand everything, and be ready for everything.”
> So It Begins: Booking Exam
The funny part was I got a little bit bored after completing the course materials and also PortSwigger labs so I decided to start playing with web applications from HackTheForce anytime I got stuck exploiting a vulnerability I will go knocking the doors of my good friend Kleiton Kurti ( a little secret “he’s a monster when it comes to webapps” 😜)…… In a nutshell, I scheduled my OSWA Exam on December 3rd 2022 at 22:00 GMT as usual of me a night owl🦉.
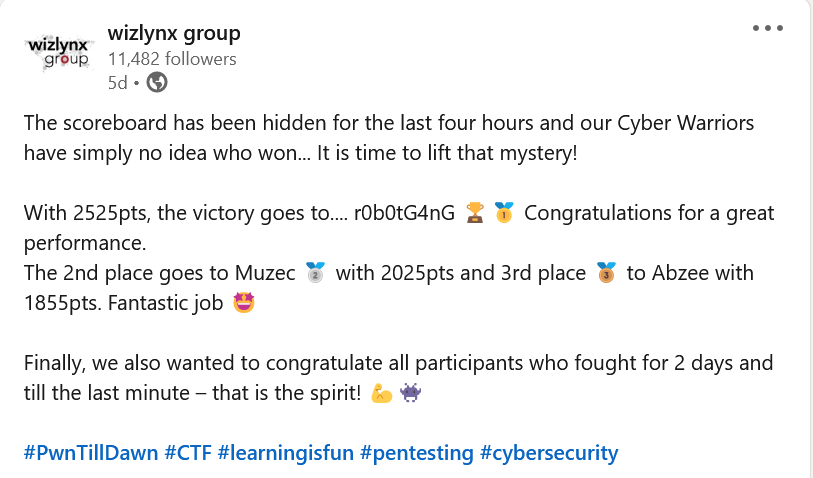
Still not satisfied with HackTheForce instances, I decided to participate in PwnTillDawn Middle East & Africa CTF Competition as an exam stress test-run hoping i will find some web applications to testm my skills…The CTF took place from November 30 2022 to December 2nd 2022… Remember my exam is scheduled on the December 3rd 2022. Luckily for me, I managed to win the competition🎉🎊🥳.
> Exam D-Day: New Age Begins
On December 3rd, 2022, I woke up at 9am (still stressed from the CTF), time to rest…. i hope so…. Well, here is my little secret: on days of execution, I try as much as possible to stay away from computers else I will end up trying to compromise vulnerable web instances. To avoid touching my laptop, i did some painting jobs at home…. At 2:00 pm GMT I took a short nap till 2:45 pm GMT then jumped back to painting work…
At 8pm exactly, I turned on my laptop checking all VM Snapshots and notes. As usual I selected a music playlist from YouTube for the exam (morale Boosters). In case you want to know, here is the playlist:
- Jahmiel Success Scary Watch Video
- Sami Yusuf - Make Me Strong Watch Video
- Zootopia - Try Everything (Lyrics, Shakira) Watch Video
At 9:30 pm GMT I logged into the proctoring tool, did all the necessary checks. Well!!! well!! well!…. the journey begins exactly at 10:15 PM GMT on December 3rd 2022.
9hrs into the exam, I managed to acquire 50 points (3 local.txt & 2 proof.txt) all I need now is an extra 20 points to pass the exam. Everything was moving smoothly and I was happy about it, I even thought i will finish the exam in the next 3/4hrs little did I know that there was a HUGE roadblock ahead. On the quest for extra 20points, I got stuck for 7hrs on the remaining targets. Almost lost hope in compromising these targets because I tried everything I learnt but none worked. I knew I was missing a piece of information from the experience I had with the OSWA lab machines anytime you get stuck for a while there are two things involved.
- You are missing a piece of the puzzle
- You are trying to exploit a wrong vulnerability (Applicationg may be vulnerable to what you have in mind but that’s not the right vulnerability to exploit)
19hrs into the exam, just when the I started to feel pressured and useless(i usually feel this way whenever things don’t go my way… This usually inspires me to push beyond my limits), I saw a vulnerability that was staring right at me all that while. A vulnerability I least thought they will implement in an exam. Once discovered, I was able to exploit this vulnerability in less than 10mins to get local.txt. 30-40mins of enumerating, I achieved code execution on the target to retrieve proof.txt. hehehe now I have 70 points (3 proof.txt and 4 local.txt) which is the required pass mark. I took a step back to doublecheck all screenshots, comments and payloads in my notes that I will need for report writing. In the process of going through the screenshots in my notes, I saw something interesting in a wfuzz screenshot. I quickly accessed that page. Guess what, it was the missing piece I needed. 45 minutes of testing and firing my payloads I achieved Code execution and was able to retrieve the fourth proof.txt, As for the 5th target…. I Won’t talk about it. I spent 7hrs+ on it exploiting a vulnerability that I was certain was the intended path, just like my OSCP exam which I found a privilege escalation point but couldn’t exploit it, the same thing happened to me on this exam.
80 points acquired, this is definitely a pass mark. The last and stressful part of the journey begins. Report writing i think is the most stressful part of an exam. Even if you are able to exploit all targets but you fail to make a good report, you are likely to fail. 20mins before the exam ended, I submitted the contents of proof.txt, used the remaining time to update my screenshots, comments and payloads in my notes. You should have seen the joy on my face hahaha I went back YouTube to listen to my favorite Jahmiel - Success Scary
On Monday December 5th, 2022 at 6:30-7pm GMT I submitted my report. Am I the only one that get scared after submitting a report? I read through my report a couple of times before and after submitting. Trying to make sure I didn’t mess up anywhere. On Wednesday December 7 2022 I finally got the email I’ve been waiting for.
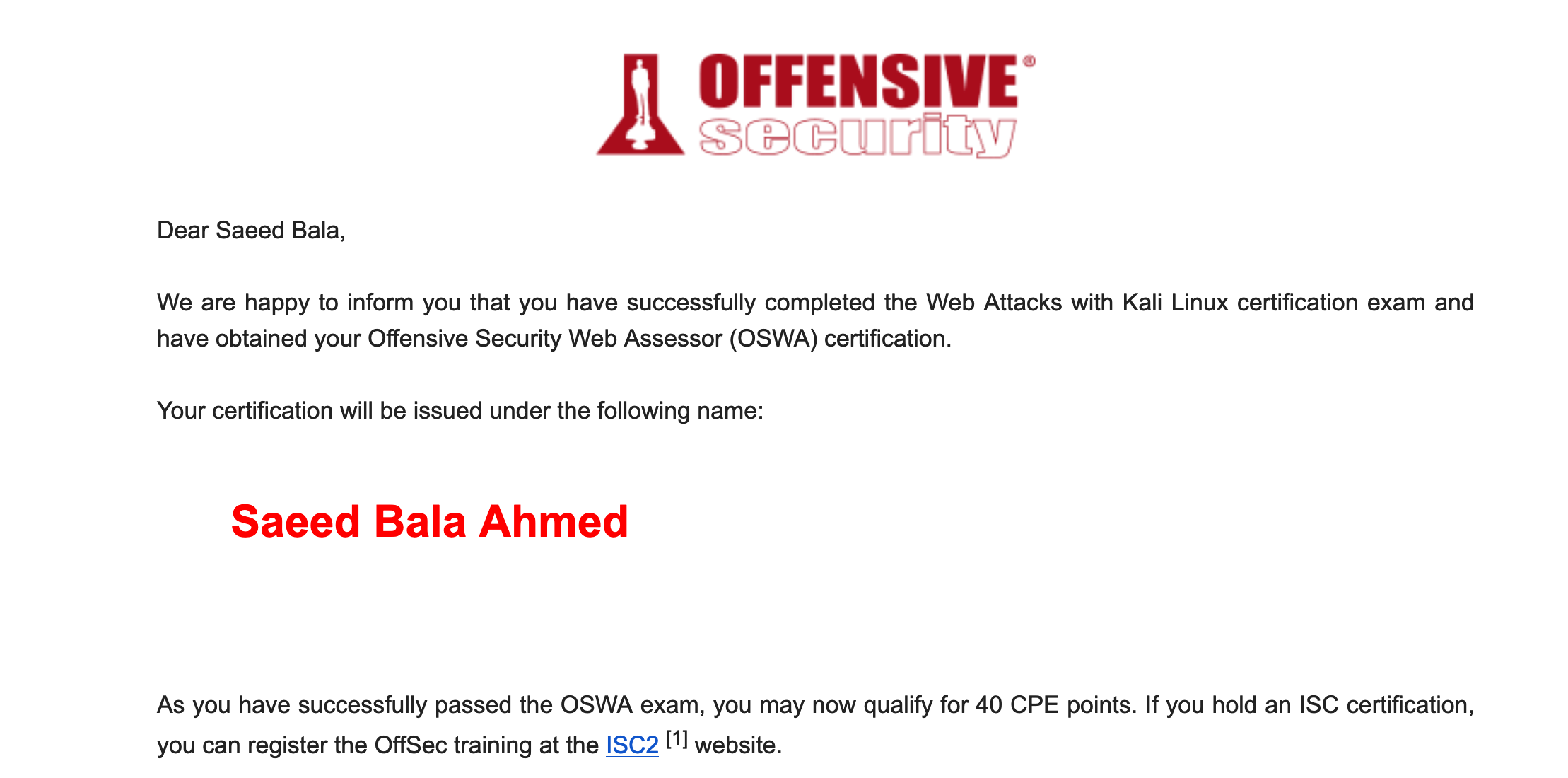
I am super excited to pass OSWA Exam on my first attempt. I will below are some unique resources that helped me throughout my OSWA journey.
> Short Advice
Make sure to read through the course materials and try your hands on all the labs. Don’t forget to make notes while you’re going through that. Read bug hunting blogs too (maybe going too far) I did that and it helped me. From these blogs I picked up various techniques in identifying and exploiting web vulnerabilities.
Remember always that “In any given moment you have two choices: Step forward into growth or step back into safety” and also keep in mind that “The hardest person you’ll ever say goodbye to is the person you used to be” Step out of that comfort zone else you won’t grow. Always dare to dream. When you dream it and believe it, you will surely achieve it.
> Special Thanks
The Lord Our God for HIS Countless Blessings. 🙏
My mentors especially DataBus & W0tw0t for the motivation. ❤️
My good friend Kleiton Kurti AKA Web-Monster 🕷️
The Ghanaian Team for their unwavering support 🤗.
The entire community of cybersecurity for their outstanding blogs and resources 👨💻.