
> Information Gathering
From nmap, we have 3 open ports which are 22 (ssh), 53 (dns) & 80 (http). Port 22 and 80 are common ports but port 53 (dns) is hardly found on targets. This is quite some good information we’ve found.

When we visit port 80, there wasn’t any webapp running there except a file note.html included in web directory.

Looking into the note.html file, there was a message from Rick to Morty. In this message, the domain name 'mortysserver.com' was mentioned.

The obvious step is to add the domain name we found from the message to our host file. To do this i typed sudo nano /etc/hosts then i added the ipaddress of the target and attached the domain name to it.

After adding the domain name to our host file, we can access the new web address http://mortysserver.com/. The vhost has a welcome message and also a statement which stands out. The statement is Is it a password? Maybe..

After digging deep for some time i thought of grabbing the background image on the http://mortysserver.com/ domain to investigate it. To download the image, i used the command wget http://mortysserver.com/screen.jpeg.

I tried exiftool and got nothing. Then i thought of trying steghide too just in case there is a hidden information in the background image. I installed steghide using the command sudo apt install steghide then i used steghide on the image file to extract hidden information. Command used was steghide extract -sf screen.jpeg. Steghide prompted for password and i hit enter on the keyboard. Luckily for us, there was really a hidden information in the image. Steghide extracted a text file called keystotheunivers.txt from the image. Reading the contents of the keystotheunivers.txt displayed a username and a password rick:WubbaLubbaDubDub1!.

The obvious place we all will try to login with credentials is ssh on port 22 right? Unfortunately, that didn’t work. Now the question is “on which service do we have to use this credential we found?”. After thinking for a while i remembered that from nmap results, we found port 53 (dns) so the only option was to query the dns service of the target. I executed the command dig mortysserver.com axfr @10.150.150.57 and from the results, we found out that there is another vhost on the target. Th new domain name we found was rickscontrolpanel.mortysserver.com.

I quickly added the new hostname rickscontrolpanel.mortysserver.com to my host file like we did earlier on. sudo nano /etc/hosts

After adding the domain name to our host file, we browsed the new domain name rickscontrolpanel.mortysserver.com and found phpMyAdmin running on this vhost.

We found credentials from the image remember? now is a good time to try it. Using the credentials, we found earlier on phpMyAdmin, we were able to login using rick:WubbaLubbaDubDub1!
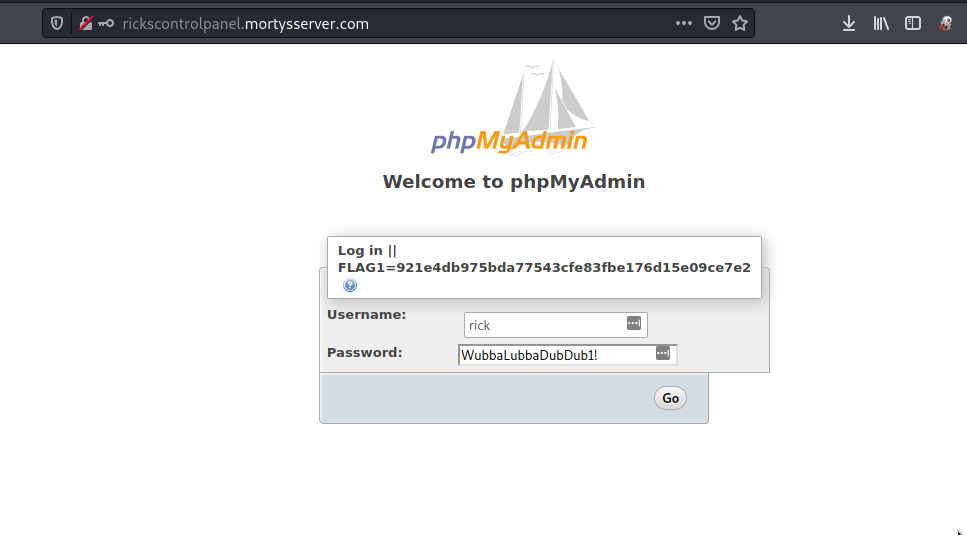
After logging in successfully and got access to the phpMyAdmin dashboard, i tried many ways to get a remote code execution manually from phpMyAdmin but i failed.

The version of phpMyAdmin running on the target is Version information: 4.8.1. I quickly googled the version and found and exploit.

The exploit we found on rapid7 indicates that phpMyAdmin v4.8.0 and v4.8.1 are vulnerable to local file inclusion, which can be exploited post-authentication to execute PHP code by application.

Start msfconsole and load the exploit module using the command use exploit/multi/http/phpmyadmin_lfi_rce. Set all required options that this exploit depends on. PASSWORD, VHOST, USERNAME, RHOST, RPORT & LHOST.

When all exploit options are set, type run or exploit in msfconsole and wait for the exploit to run against the target. You should be presented with a spawned shell in msfconsole on the target.

Reference: PwnTillDawn Online battlefield